
Explanation of Solution
Given: The project name music-organizer-v1 and the class name MusicOrganizer.
To find: The way to store the names of some audio files and the number of files returned by the numberOfFiles.
Solution:
Open BlueJ and then open a new project named Music-organizer-v1.
To make the instance of the class MusicOrganizer:
Right-click on the class MusicOrganizer.
Select construct new MusicOrganizer() of the class MusicOrganizer to make its instance.
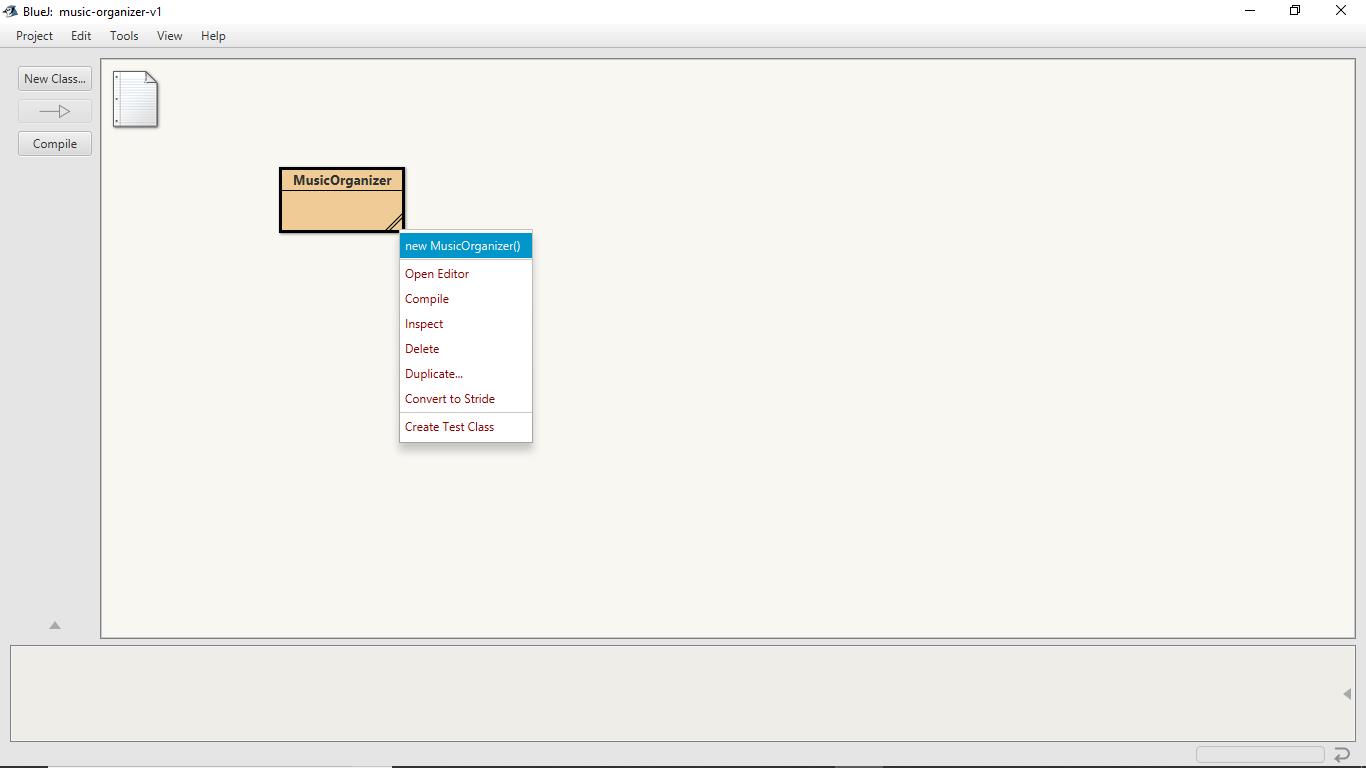
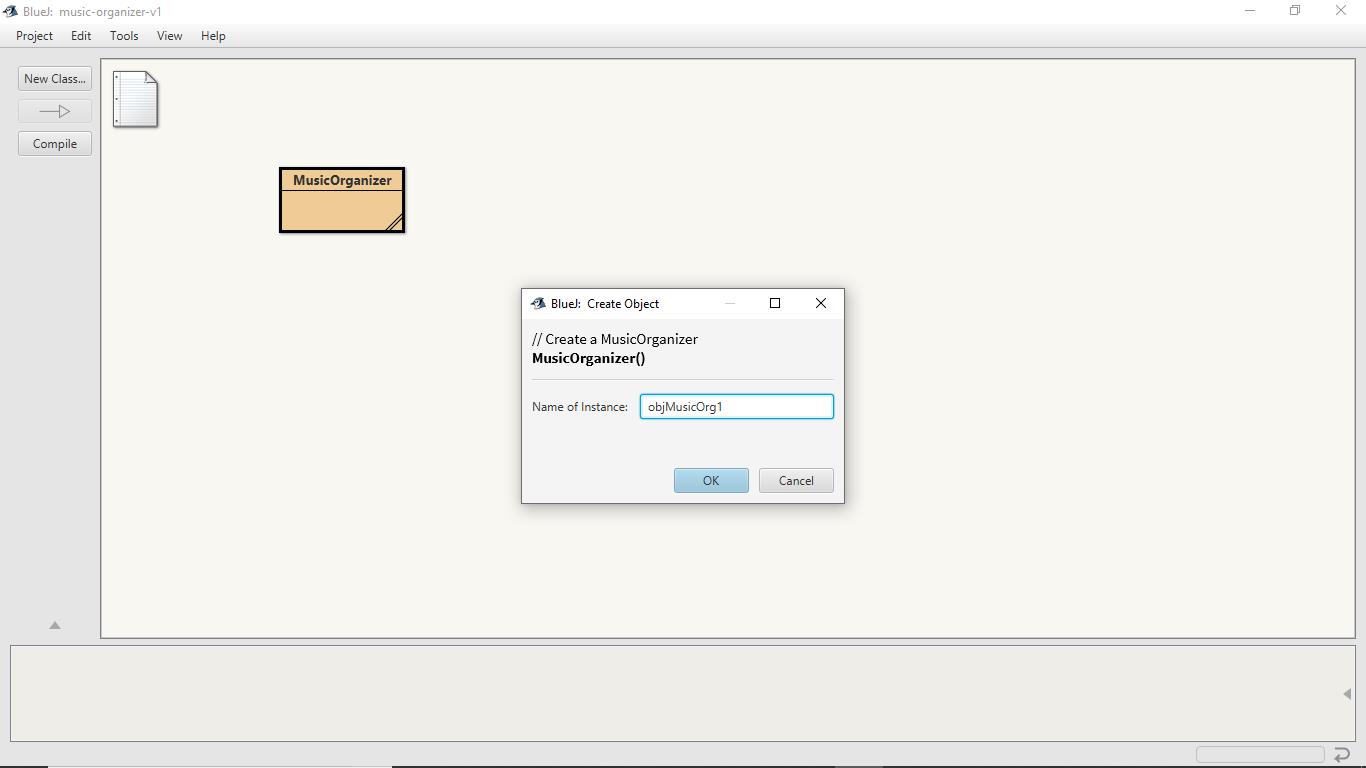
A window would show up which will ask for the name of the instance.
So, enter the name of the instance as objMusicOrg1 in place of default instance name and click on OK button.
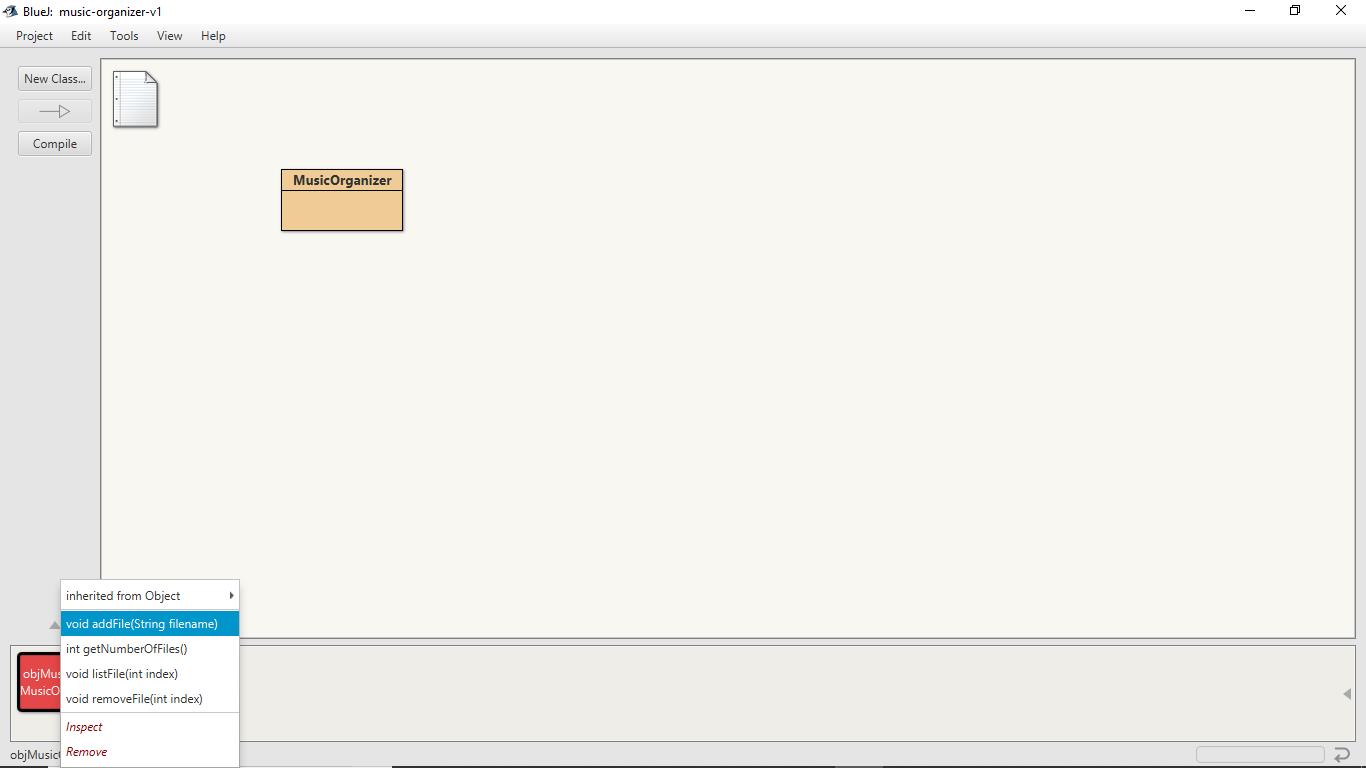
After that, right-click on that instance residing on the object bench and then click on the method addFile to add some file names to the instance.
A window would show up asking for the name of the file to add it to the collection.
Enter any file name (along with its location) within the text box linked with it and then click on the OK button.
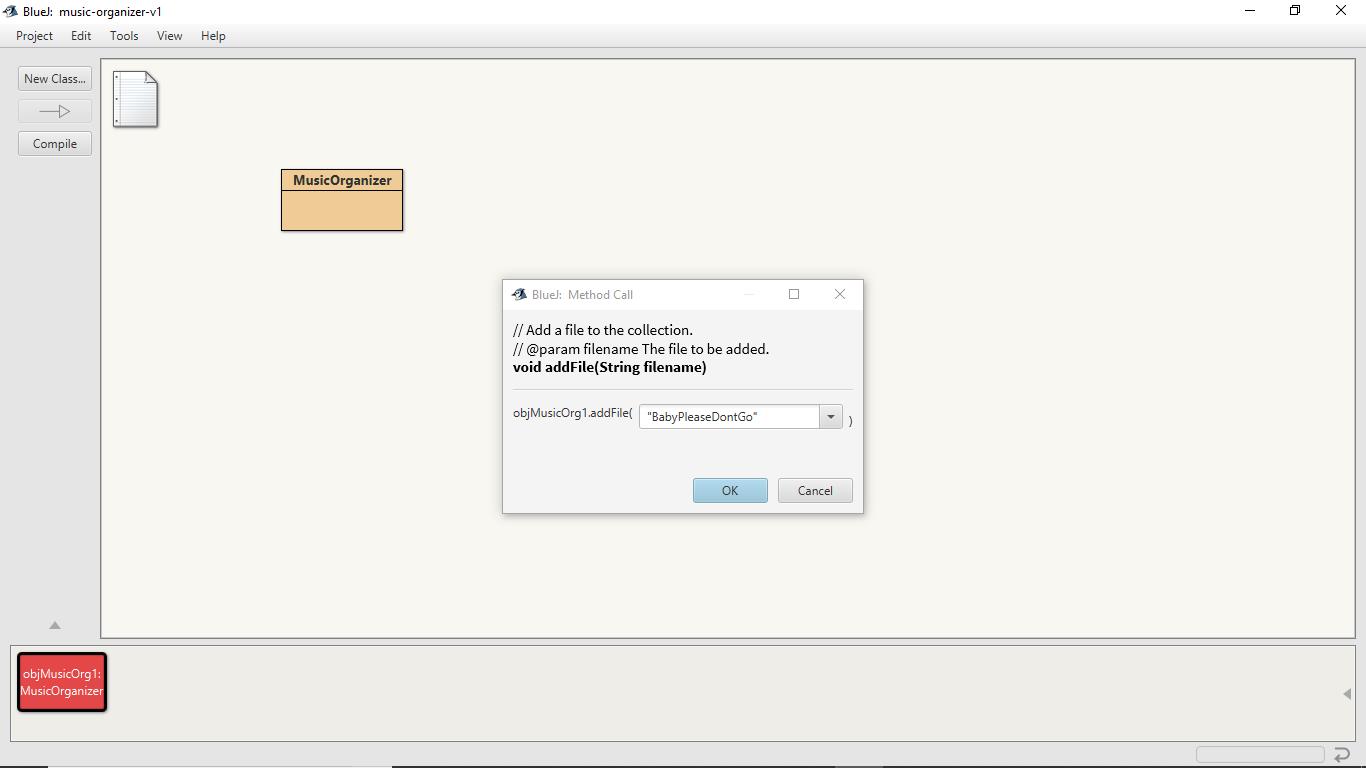
Repeat this procedure two times to add two file names to the collection.
To examine the number of files stored, right-click on the instance objMusicOrg1 of the class MusicOrganizer and then click on the method getNumberOfFiles.
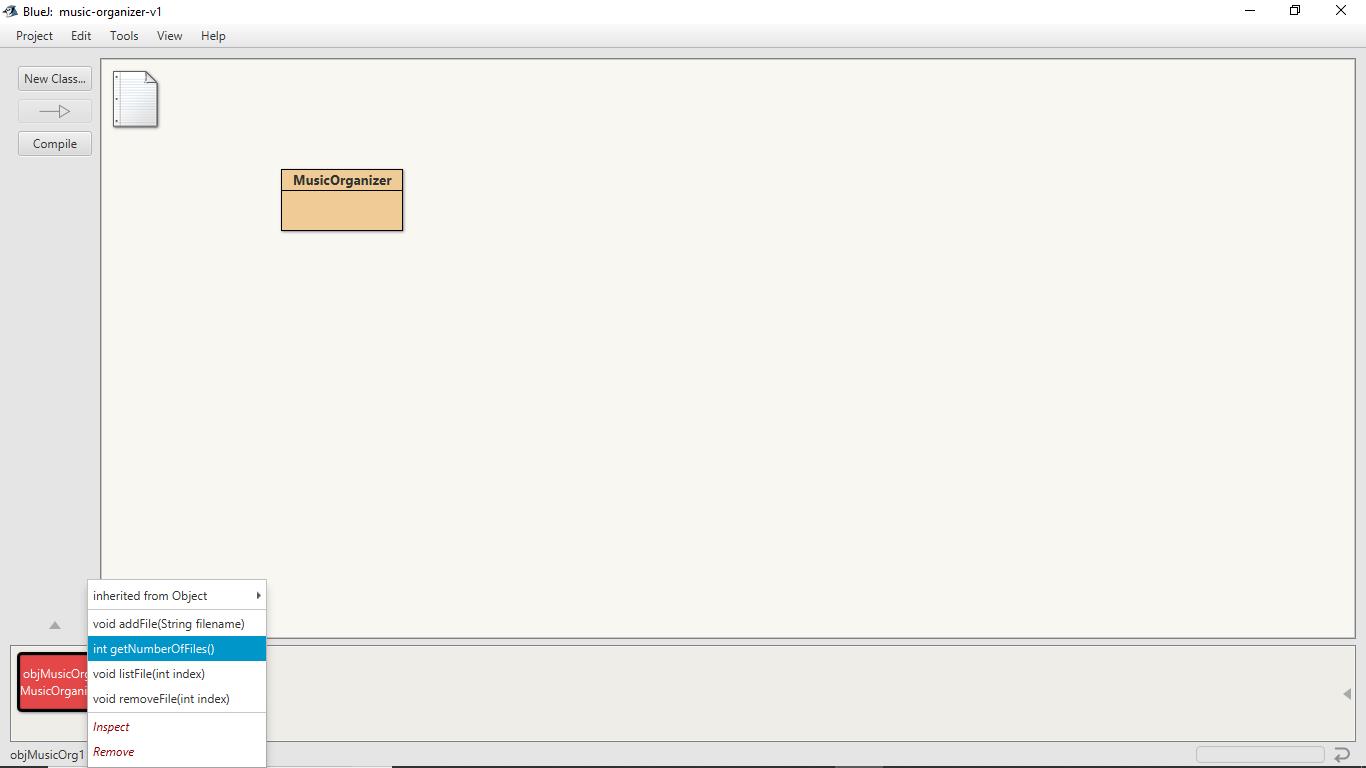
As we have added two files to the collection, the method result of getNumberOfFiles returned 2.
To print the files stored in the collection of the class instance objMusicOrg1, we require to method call listFile.
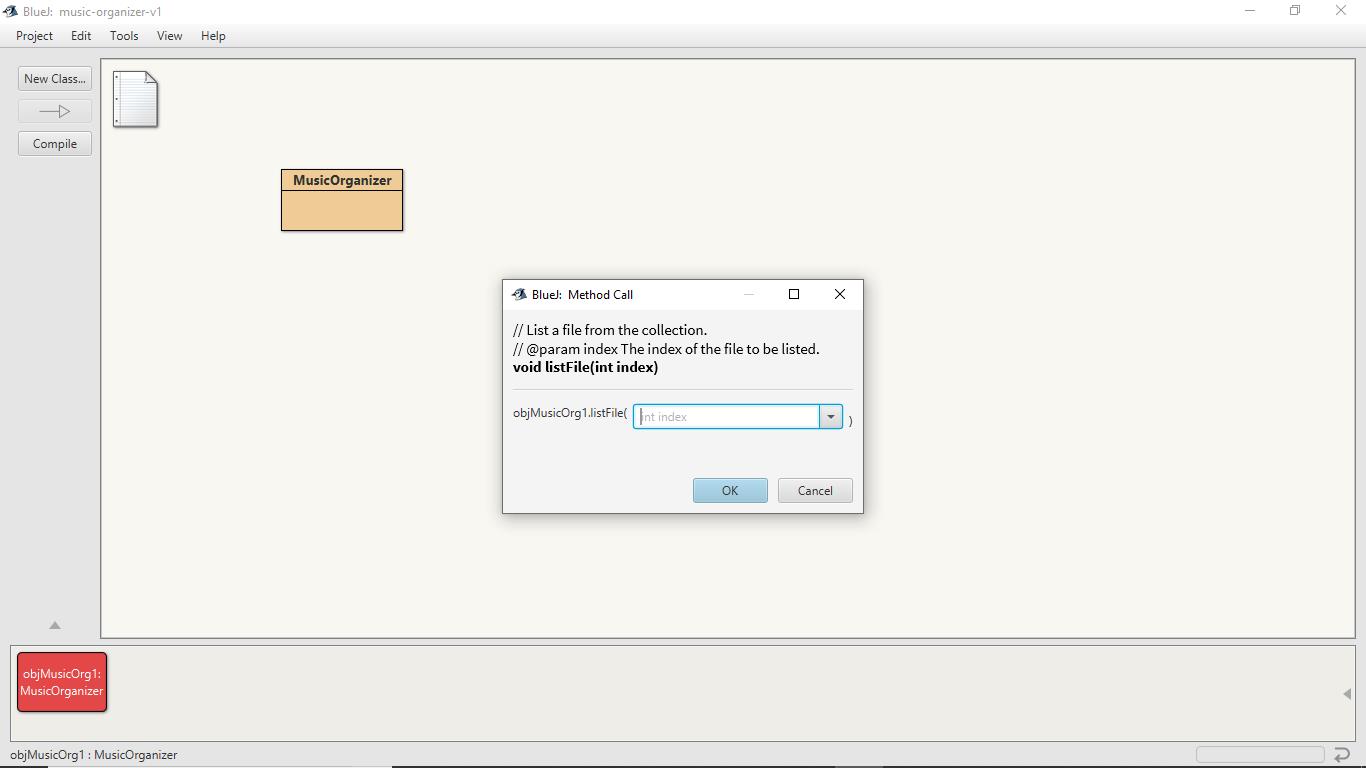
When the method listFile is called, a window would show up which will ask for the file index. Since we have stored 2 files in the collection and the indexing in any collection starts form 0, starting from 0 the index will end at 1, that is, from 0 to 1.
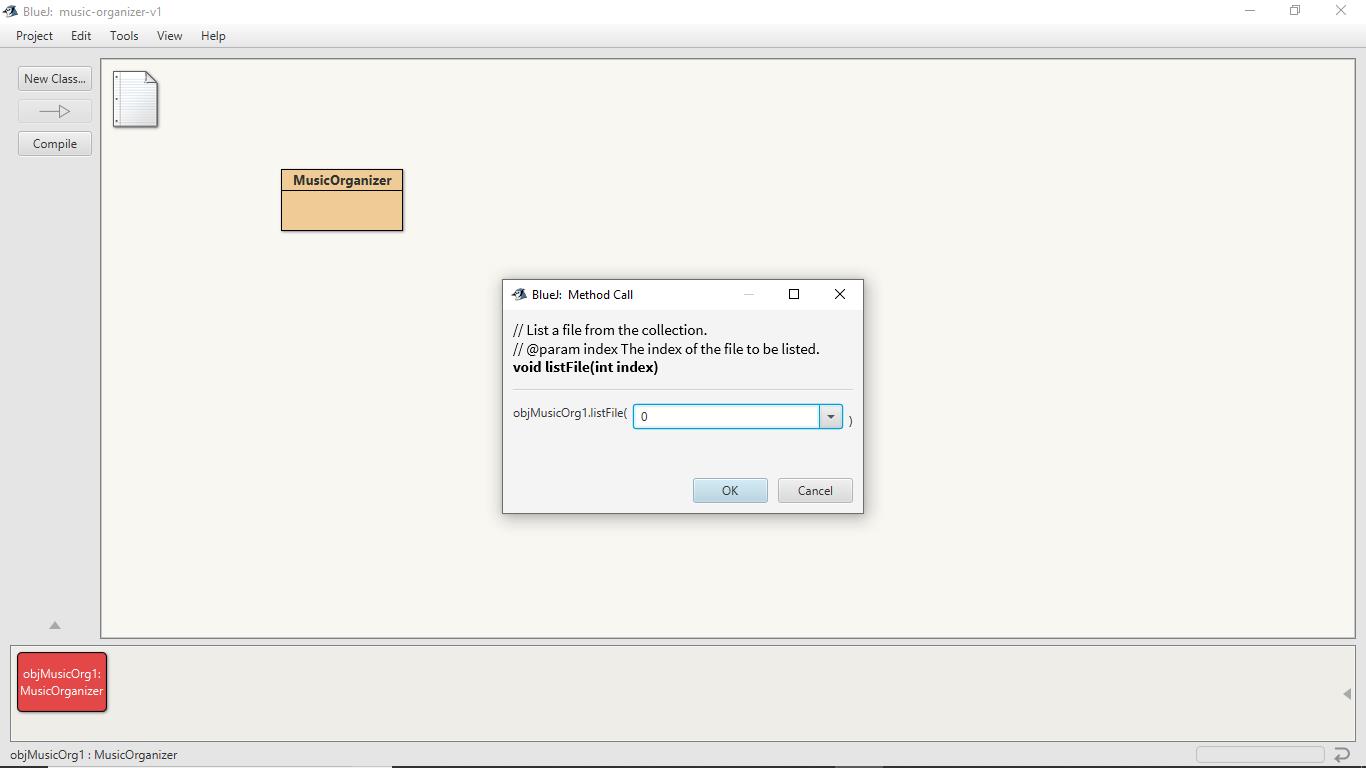
Here, 0 shows the first file index and 1 shows the second file index.
Output:
After clicking on the OK button in the window shown above, we get the following result.

Modifying the index at the time of calling the method listFile, we get the filenames stored in that index on the Terminal Window.
Want to see more full solutions like this?
Chapter 4 Solutions
Objects First with Java: A Practical Introduction Using BlueJ (6th Edition)
- 2:21 m Ο 21% AlmaNet WE ARE HIRING Experienced Freshers Salesforce Platform Developer APPLY NOW SEND YOUR CV: Email: hr.almanet@gmail.com Contact: +91 6264643660 Visit: www.almanet.in Locations: India, USA, UK, Vietnam (Remote & Hybrid Options Available)arrow_forwardProvide a detailed explanation of the architecture on the diagramarrow_forwardhello please explain the architecture in the diagram below. thanks youarrow_forward
- Complete the JavaScript function addPixels () to calculate the sum of pixelAmount and the given element's cssProperty value, and return the new "px" value. Ex: If helloElem's width is 150px, then calling addPixels (hello Elem, "width", 50) should return 150px + 50px = "200px". SHOW EXPECTED HTML JavaScript 1 function addPixels (element, cssProperty, pixelAmount) { 2 3 /* Your solution goes here *1 4 } 5 6 const helloElem = document.querySelector("# helloMessage"); 7 const newVal = addPixels (helloElem, "width", 50); 8 helloElem.style.setProperty("width", newVal); [arrow_forwardSolve in MATLABarrow_forwardHello please look at the attached picture. I need an detailed explanation of the architecturearrow_forward
- Information Security Risk and Vulnerability Assessment 1- Which TCP/IP protocol is used to convert the IP address to the Mac address? Explain 2-What popular switch feature allows you to create communication boundaries between systems connected to the switch3- what types of vulnerability directly related to the programmer of the software?4- Who ensures the entity implements appropriate security controls to protect an asset? Please do not use AI and add refrencearrow_forwardFind the voltage V0 across the 4K resistor using the mesh method or nodal analysis. Note: I have already simulated it and the value it should give is -1.714Varrow_forwardResolver por superposicionarrow_forward
- Describe three (3) Multiplexing techniques common for fiber optic linksarrow_forwardCould you help me to know features of the following concepts: - commercial CA - memory integrity - WMI filterarrow_forwardBriefly describe the issues involved in using ATM technology in Local Area Networksarrow_forward
- Np Ms Office 365/Excel 2016 I NtermedComputer ScienceISBN:9781337508841Author:CareyPublisher:Cengage
 EBK JAVA PROGRAMMINGComputer ScienceISBN:9781305480537Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781305480537Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT - COMPREHENSIVE MICROSOFT OFFICE 365 EXCEComputer ScienceISBN:9780357392676Author:FREUND, StevenPublisher:CENGAGE LProgramming Logic & Design ComprehensiveComputer ScienceISBN:9781337669405Author:FARRELLPublisher:Cengage
 C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning





