
1)
To determine: Whether anyone can read the message.
Introduction:
1)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
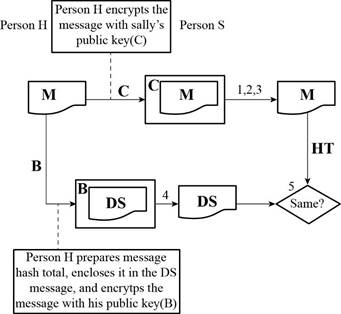
Given diagram:
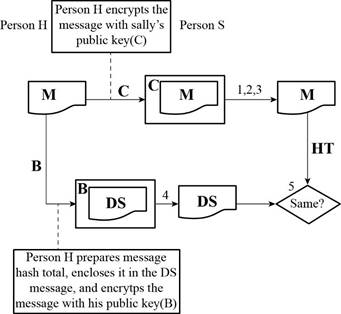
Here,
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether anyone can read the message:
Not everyone can read the message. Only the person who has the private key of Person S can be able to open the message.
2)
To determine: Whether Person S can be sure that the message is from Person H.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
2)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
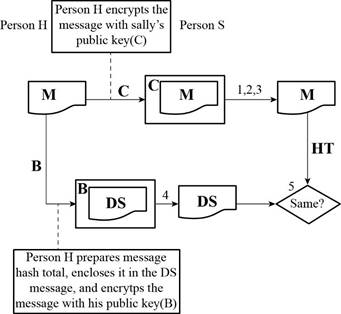
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether Person S can be sure that the message is from Person H:
Anyone with the public key of Person S can be able to send the message
3)
To determine: Whether digital signature message is secret.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
3)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
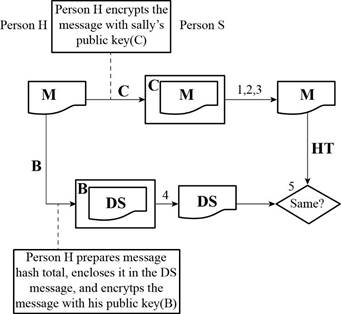
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether a digital signature message is secret:
Anyone with the public key of Person H can be able to open the digital signature message.
4)
To determine: Whether someone other than Person H can send the digital signature message.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
4)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
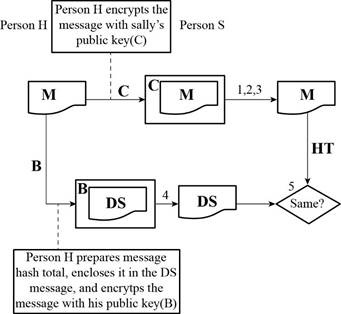
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether someone other than Person H can send the digital signature message:
A person with the private key of Person H can be able to send the digital signature message.
5)
To determine: How Person S know that the message has not been corrupted in transit.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
5)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine how Person S know that the message has not been corrupted in transit:
If the hash total of digital signature equals the hash total that Person S calculated from the message then the message has not been corrupted in transit.
6)
To determine: The sub-part that is related to authenticity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
6)
Explanation of Solution
Determine the subpart that is related to authenticity:
Subpart (2) and Subpart (4) are about authenticity.
7)
To determine: The sub-part that is related to integrity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
7)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to integrity:
Subpart (5) is about integrity.
8)
To determine: The sub-part that is related to confidentiality.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
8)
Explanation of Solution
Given diagram:
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to confidentiality:
Subpart (1) and Subpart (3) are about the confidentially.
Want to see more full solutions like this?
Chapter 9 Solutions
Accounting Information Systems
- Principles of Accounting Volume 1AccountingISBN:9781947172685Author:OpenStaxPublisher:OpenStax College
 Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,
Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning, Auditing: A Risk Based-Approach (MindTap Course L...AccountingISBN:9781337619455Author:Karla M Johnstone, Audrey A. Gramling, Larry E. RittenbergPublisher:Cengage Learning
Auditing: A Risk Based-Approach (MindTap Course L...AccountingISBN:9781337619455Author:Karla M Johnstone, Audrey A. Gramling, Larry E. RittenbergPublisher:Cengage Learning  Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning
Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning



