
COMPUTER SCIENCE ILLUMIN.-TEXT
7th Edition
ISBN: 9781284156010
Author: Dale
Publisher: Jones & Barlett
expand_more
expand_more
format_list_bulleted
Question
Chapter 8, Problem 47E
Program Plan Intro
Binary search tree:
- Binary search tree is a tree; the nodes are sorted in the semantic order.
- Binary search tree nodes can have zero, one, or two children.
- Node without children is called a leaf or end node.
- A node that does not have a superior node is called a root node or starting node.
- In binary search tree, the left subtree contains the nodes lesser than the root node.
- The right subtree contains the nodes greater than the root node.
- The binary search will performed until finding a search node or reaching the end of the tree.
Expert Solution & Answer
Explanation of Solution
Insertion of elements in the binary search tree:
Given elements to construct a binary search tree are as follows:
50, 72, 96, 107, 26, 12, 11, 9, 2, 10, 25, 51, 16, 17, 95.
Step 1:
Insert the element 50, which is the root node of a binary search tree.

Step 2:
Next element is 72, which is greater than root node element 50, so insert the element 72 as the right child of the root node.
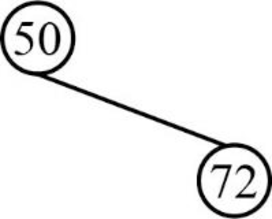
Step 3:
- Next element is 96, which is greater than root node element 50, so insert the element 96 as the right child of the root node.
- The root node already contains the element 72 as the right child and the element 96 is greater than the element 72.
- So, insert the element 96 as the right child of 72.
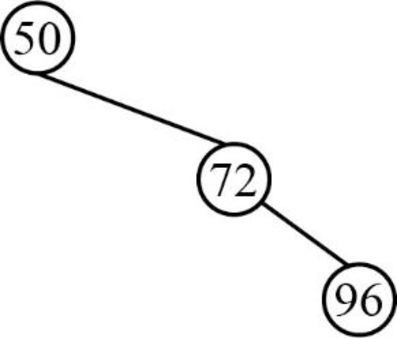
Step 4:
- Next element is 107, which is greater than root node element 50, so insert the element 107 as the right child of the root node.
- The root node already contains the element 72 as the right child and the element 107 is greater than the element 72.
- The element 72 already contains the element 96 as the right child and the element 107 is greater than the element 96.
- So, insert the element 107 as the right child of 96.
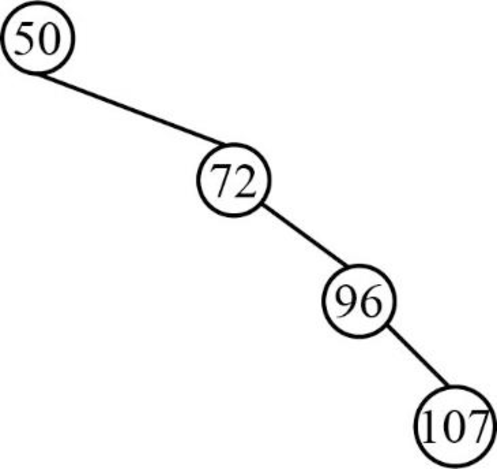
Step 5:
Next element is 26, which is less than root node value 50, so insert the element 26 as the left child of the root node.
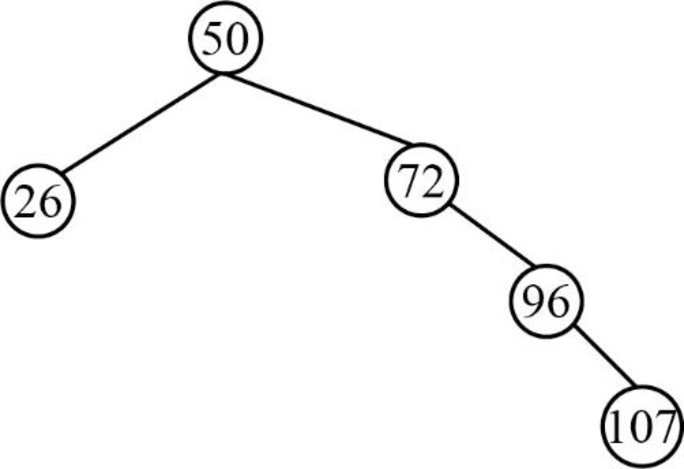
Step 6:
- Next element is 12, which is less than the root node value 50, so insert the element 12 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 12 is less than the element 26.
- So, insert the element 12 as left child of the element 26.
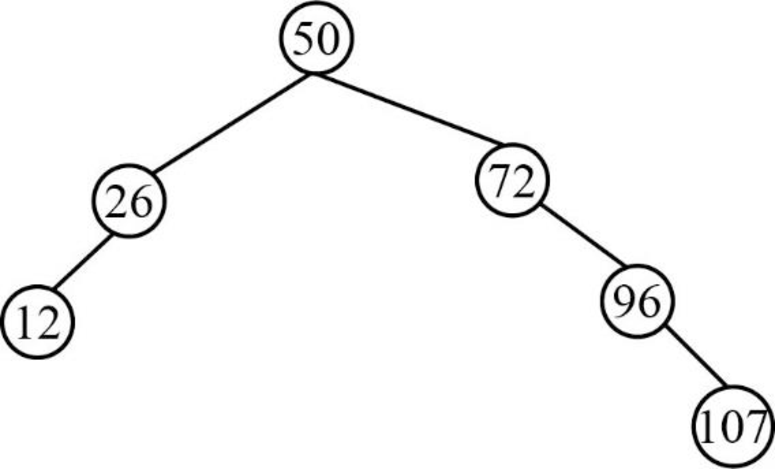
Step 7:
- Next element is 11, which is less than the root node value 50, so insert the element 11 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 11 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 11 is lesser than the element 12.
- So, insert the element 11 as left child of the element 12.
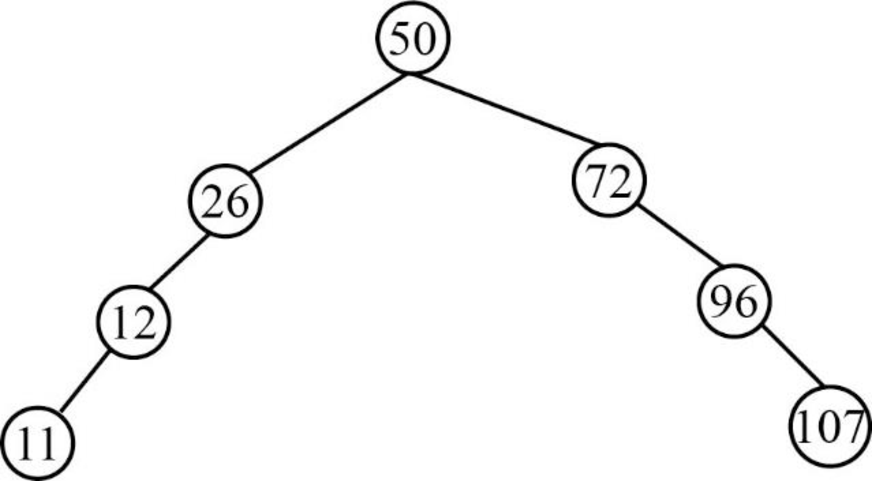
Step 8:
- Next element is 9, which is less than the root node value 50, so insert the element 9 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 9 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 9 is lesser than the element 12.
- The element 12 already contains the element 11 as the left child and the element 9 is lesser than the element 11.
- So, insert the element 9 as left child of the element 11.
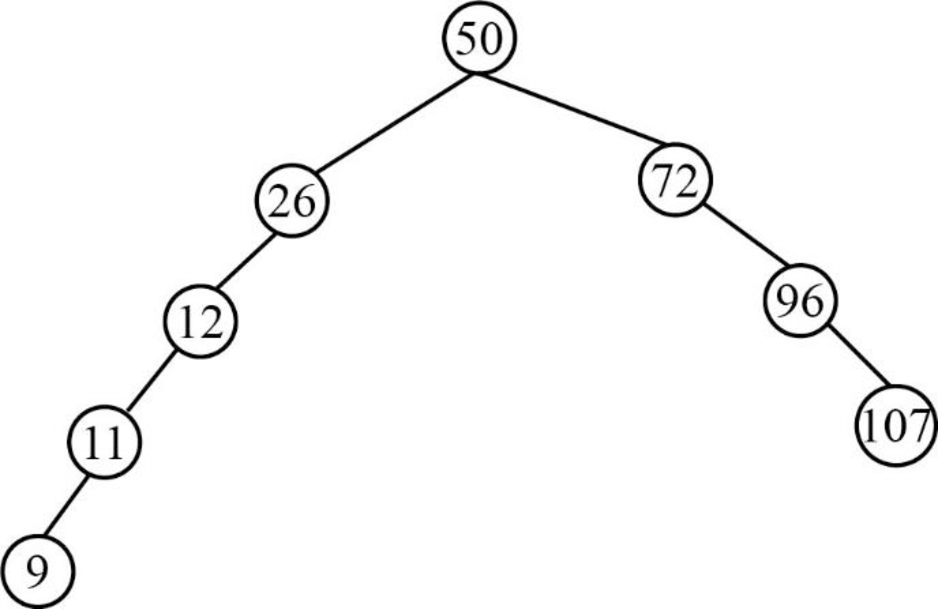
Step 9:
- Next element is 2, which is less than the root node value 50, so insert the element 2 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 2 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 2 is lesser than the element 12.
- The element 12 already contains the element 11 as the left child and the element 2 is lesser than the element 11.
- The element 11 already contains the element 9 as the left child and the element 2 is lesser than the element 9.
- So, insert the element 2 as left child of the element 9.
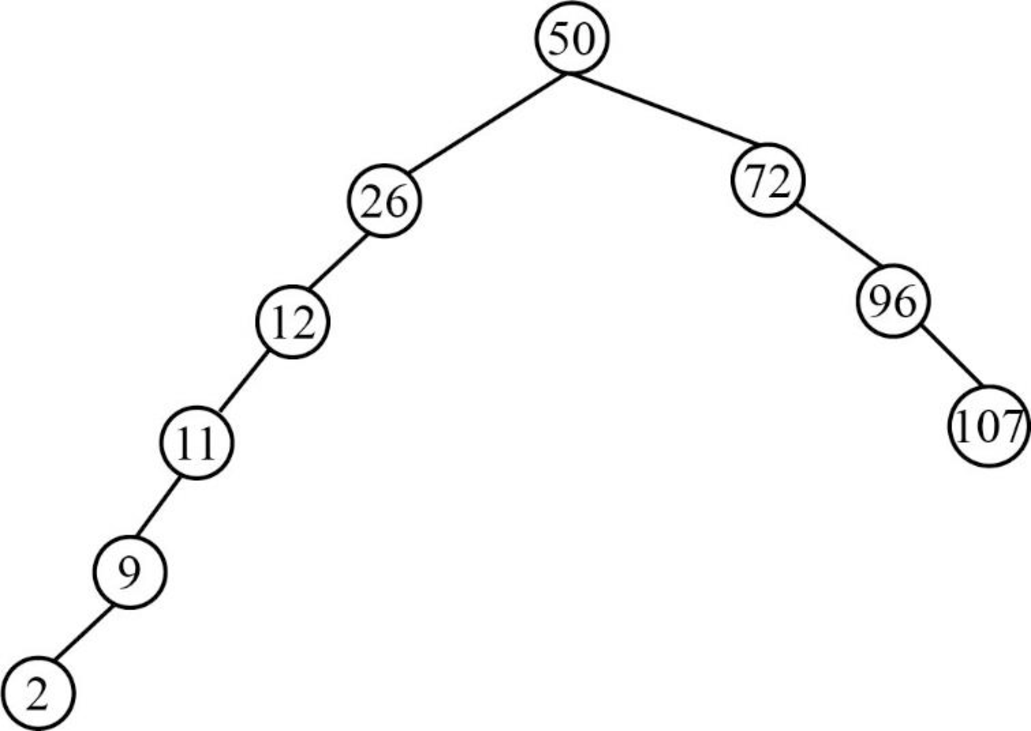
Step 10:
- Next element is 10, which is less than the root node value 50, so insert the element 10 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 10 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 10 is lesser than the element 12.
- The element 12 already contains the element 11 as the left child and the element 10 is lesser than the element 11.
- The element 11 already contains the element 9 as the left child and the element 10 is greater than the element 9.
- So, insert the element 10 as right child of the element 9.
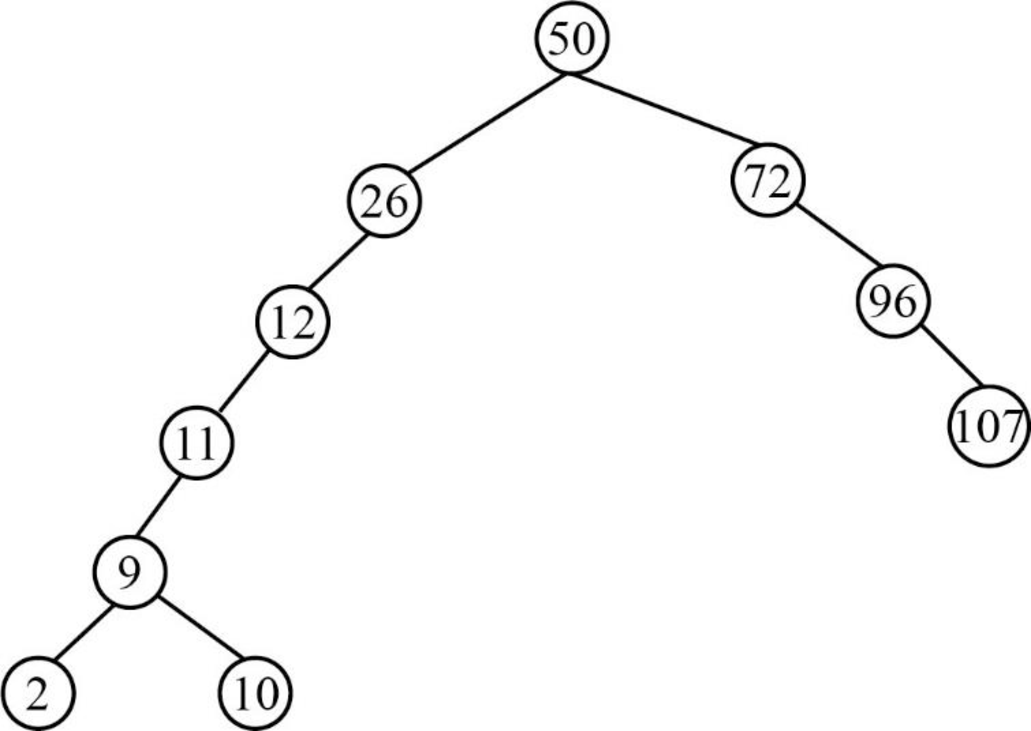
Step 11:
- Next element is 25, which is less than the root node value 50, so insert the element 25 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 25 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 25 is greater than the element 12.
- So, insert the element 25 as right child of the element 12.
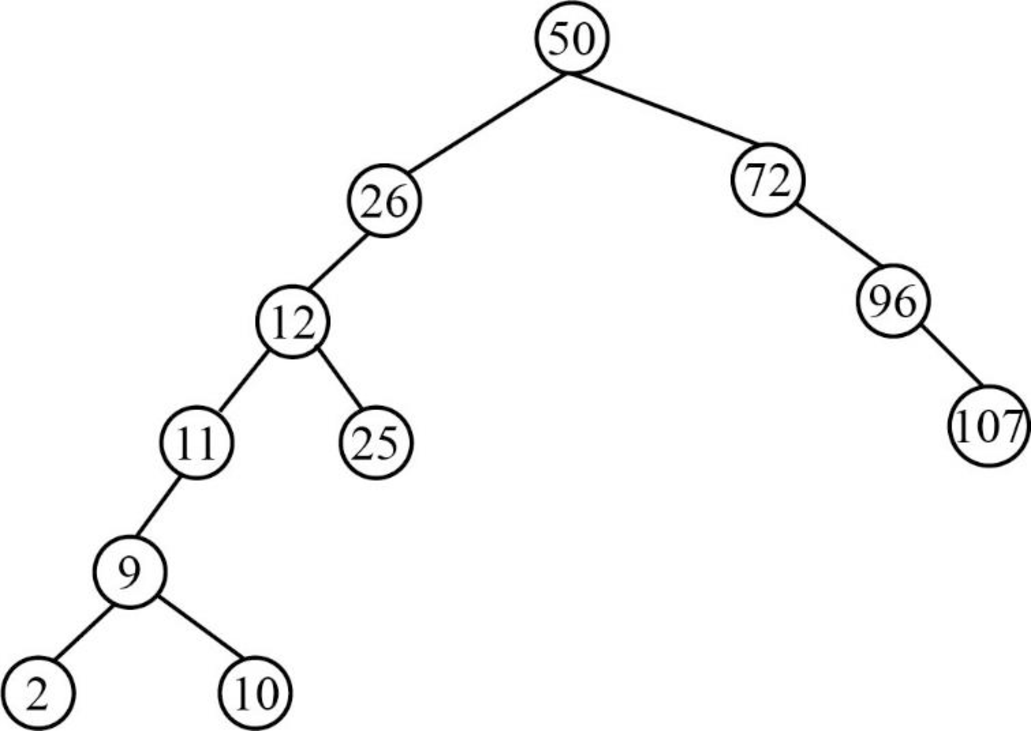
Step 12:
- Next element is 51, which is greater than root node element 50, so insert the element 51 as the right child of the root node.
- The root node already contains the element 72 as the right child and the element 51 is lesser than the element 72.
- So, insert the element 51 as the left child of 72.
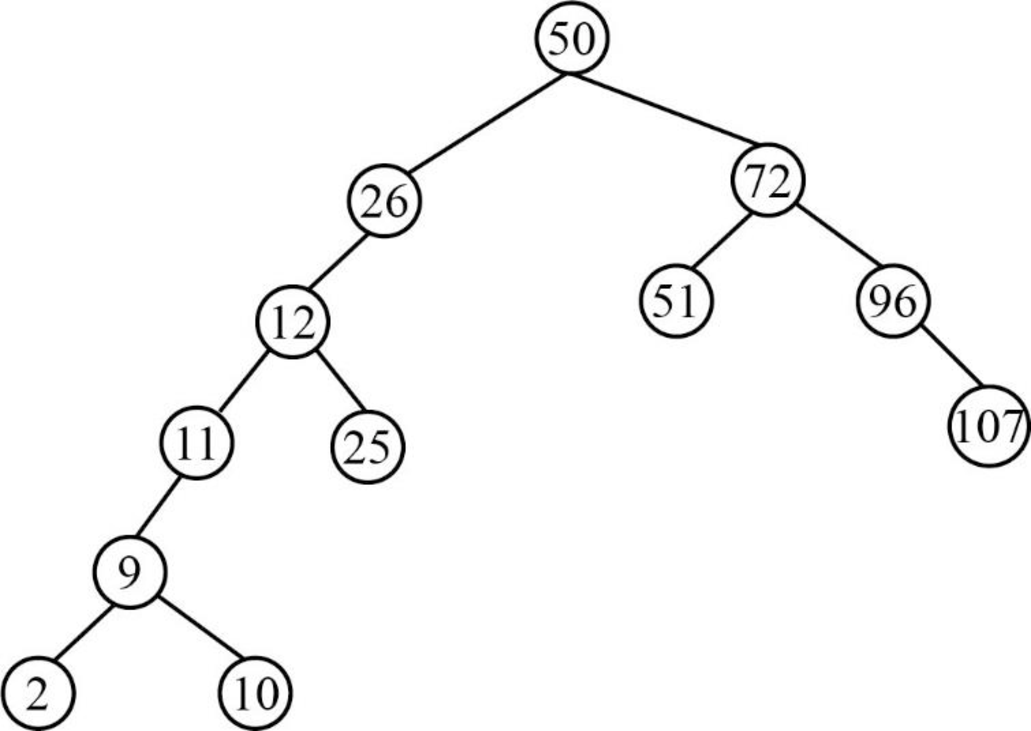
Step 13:
- Next element is 16, which is less than the root node value 50, so insert the element 16 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 16 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 16 is greater than the element 12.
- The element 12 already contains the element 25 as the right child and the element 16 is lesser than the element 25.
- So, insert the element 16 as left child of the element 25.
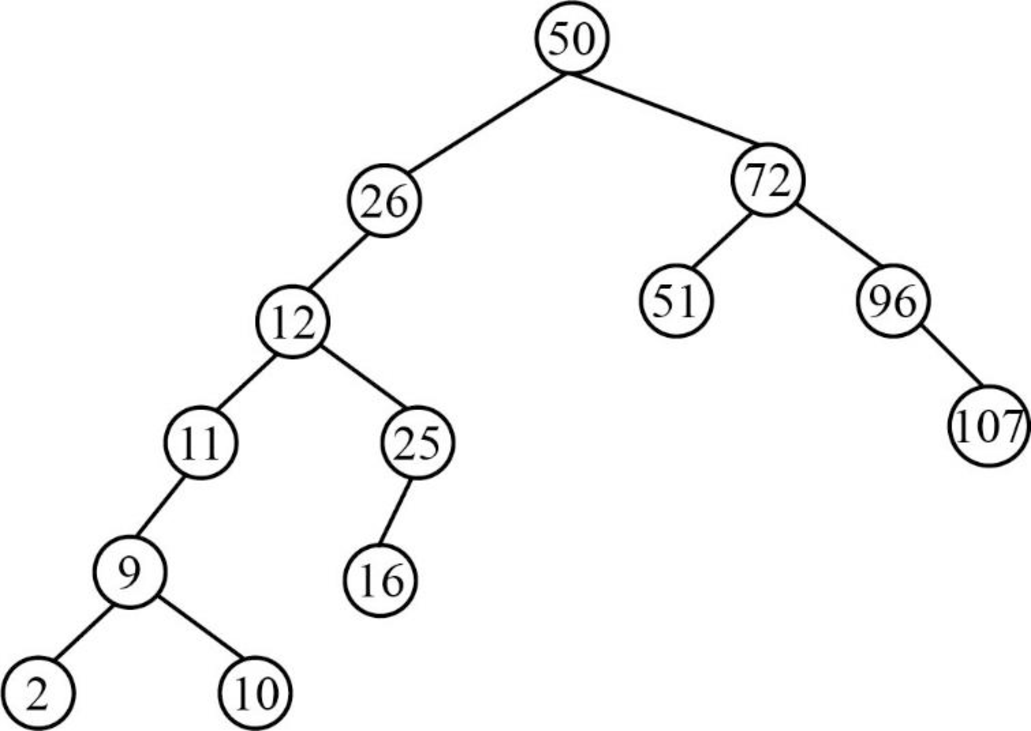
Step 14:
- Next element is 17, which is less than the root node value 50, so insert the element 17 as left child of the root node.
- The root node already contains the element 26 as the left child and the element 17 is less than the element 26.
- The element 26 already contains the element 12 as the left child and the element 17 is greater than the element 12.
- The element 12 already contains the element 25 as the right child and the element 17 is lesser than the element 25.
- The element 25 already contains the element 16 as the left child and the element 17 is greater than the element 16.
- So, insert the element 17 as right child of the element 16.
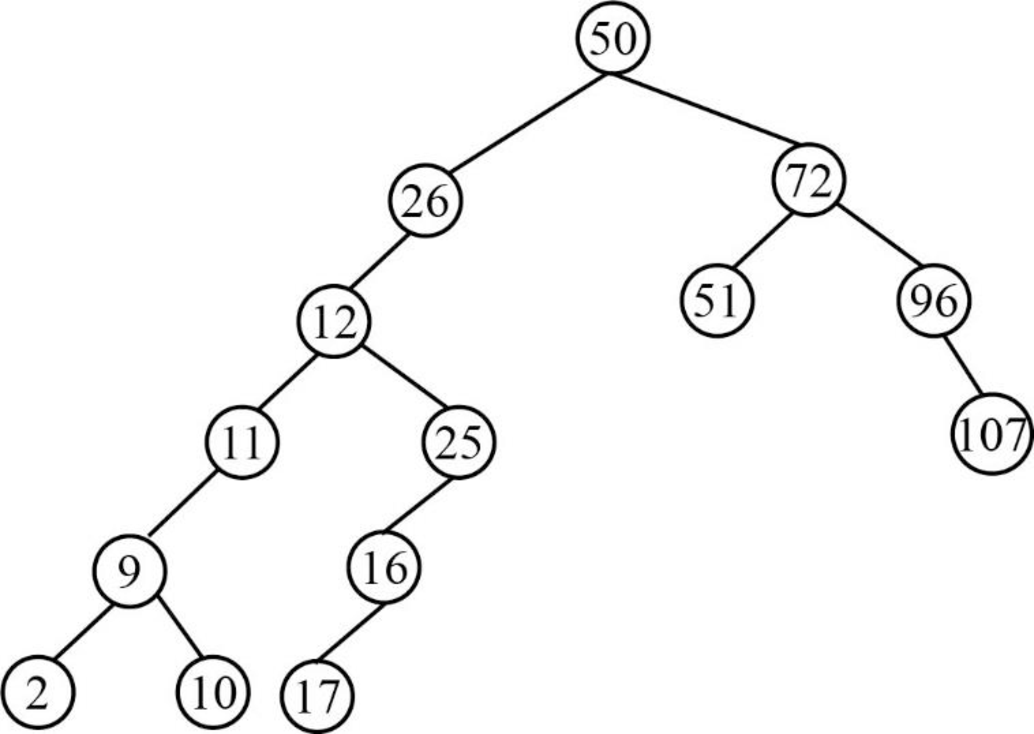
Step 15:
- Next element is 95, which is greater than root node element 50, so insert the element 95 as the right child of the root node.
- The root node already contains the element 72 as the right child and the element 95 is greater than the element 72.
- The element 72 already contains the element 96 as the right child and the element 95 is lesser than the element 96.
- So, insert the element 95 as the left child of 96.
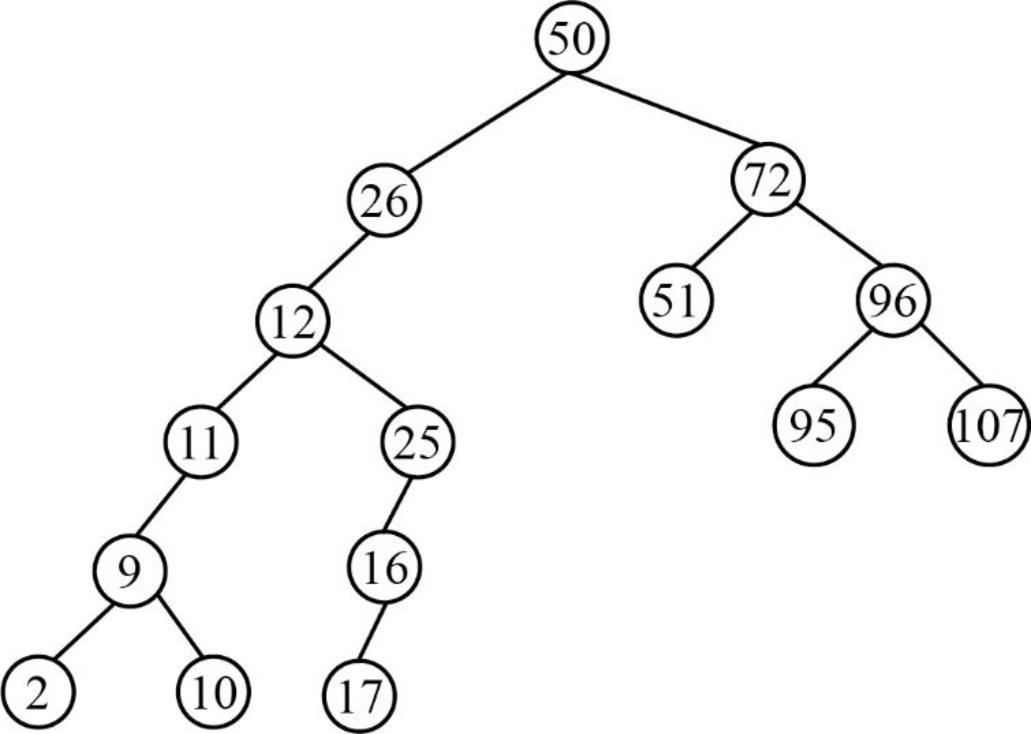
Therefore, the above tree is the final constructed binary search tree for the given elements.
Want to see more full solutions like this?
Subscribe now to access step-by-step solutions to millions of textbook problems written by subject matter experts!
Students have asked these similar questions
The Horse table has the following columns:
ID - integer, auto increment, primary key
RegisteredName - variable-length string
Breed - variable-length string
Height - decimal number
BirthDate - date
Delete the following rows:
Horse with ID 5
All horses with breed Holsteiner or Paint
All horses born before March 13, 2013
To confirm that the deletes are correct, add the SELECT * FROM HORSE; statement.
Why is Linux popular? What would make someone choose a Linux OS over others? What makes a server? How is a server different from a workstation? What considerations do you have to keep in mind when choosing between physical, hybrid, or virtual server and what are the reasons to choose a virtual installation over the other options?
Objective you will:
1. Implement a Binary Search Tree (BST) from scratch, including the Big Five (Rule of Five)
2. Implement the TreeSort algorithm using a in-order traversal to store sorted elements in a vector.
3. Compare the performance of TreeSort with C++'s std::sort on large datasets.
Part 1: Understanding TreeSort How TreeSort Works TreeSort is a comparison-based sorting algorithm that leverages a Binary Search Tree (BST):
1. Insert all elements into a BST (logically sorting them).
2. Traverse the BST in-order to extract elements in sorted order.
3. Store the sorted elements in a vector.
Time Complexity
Operation Average Case Worst Case (Unbalanced Tree)Insertion 0(1log n) 0 (n)Traversal (Pre-order) 0(n) 0 (n)Overall Complexity 0(n log n) 0(n^2) (degenerated tree)
Note: To improve performance, you could use a…
Chapter 8 Solutions
COMPUTER SCIENCE ILLUMIN.-TEXT
Ch. 8 - Prob. 1ECh. 8 - Prob. 2ECh. 8 - Prob. 3ECh. 8 - Prob. 4ECh. 8 - Prob. 5ECh. 8 - Prob. 6ECh. 8 - Prob. 7ECh. 8 - Prob. 8ECh. 8 - Prob. 9ECh. 8 - Prob. 10E
Ch. 8 - Prob. 11ECh. 8 - Prob. 12ECh. 8 - Prob. 13ECh. 8 - Prob. 14ECh. 8 - Prob. 15ECh. 8 - Prob. 16ECh. 8 - Prob. 17ECh. 8 - Prob. 18ECh. 8 - Prob. 19ECh. 8 - Prob. 20ECh. 8 - Prob. 21ECh. 8 - Prob. 22ECh. 8 - Prob. 23ECh. 8 - Prob. 24ECh. 8 - Prob. 25ECh. 8 - Prob. 26ECh. 8 - Prob. 27ECh. 8 - Prob. 28ECh. 8 - Prob. 29ECh. 8 - Prob. 30ECh. 8 - Prob. 31ECh. 8 - Prob. 32ECh. 8 - Prob. 33ECh. 8 - Prob. 34ECh. 8 - Prob. 35ECh. 8 - Prob. 36ECh. 8 - Prob. 37ECh. 8 - Prob. 38ECh. 8 - Prob. 39ECh. 8 - Prob. 40ECh. 8 - Prob. 41ECh. 8 - Prob. 42ECh. 8 - Prob. 43ECh. 8 - Prob. 44ECh. 8 - Prob. 45ECh. 8 - Prob. 46ECh. 8 - Prob. 47ECh. 8 - Prob. 48ECh. 8 - Prob. 49ECh. 8 - Prob. 50ECh. 8 - Prob. 51ECh. 8 - Prob. 52ECh. 8 - Prob. 53ECh. 8 - Prob. 54ECh. 8 - Prob. 55ECh. 8 - Prob. 56ECh. 8 - Prob. 57ECh. 8 - Prob. 58ECh. 8 - Prob. 59ECh. 8 - Prob. 60ECh. 8 - Prob. 61ECh. 8 - Prob. 62ECh. 8 - Prob. 66ECh. 8 - Prob. 67ECh. 8 - Prob. 68ECh. 8 - Prob. 69ECh. 8 - Prob. 1TQCh. 8 - Prob. 2TQCh. 8 - Prob. 4TQ
Knowledge Booster
Similar questions
- I need help fixing the minor issue where the text isn't in the proper place, and to ensure that the frequency cutoff is at the right place. My code: % Define frequency range for the plot f = logspace(1, 5, 500); % Frequency range from 10 Hz to 100 kHz w = 2 * pi * f; % Angular frequency % Parameters for the filters - let's adjust these to get more reasonable cutoffs R = 1e3; % Resistance in ohms (1 kΩ) C = 1e-6; % Capacitance in farads (1 μF) % For bandpass, we need appropriate L value for desired cutoffs L = 0.1; % Inductance in henries - adjusted for better bandpass response % Calculate cutoff frequencies first to verify they're in desired range f_cutoff_RC = 1 / (2 * pi * R * C); f_resonance = 1 / (2 * pi * sqrt(L * C)); Q_factor = (1/R) * sqrt(L/C); f_lower_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) + 1/(2*Q_factor)); f_upper_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) - 1/(2*Q_factor)); % Transfer functions % Low-pass filter (RC) H_low = 1 ./ (1 + 1i * w *…arrow_forwardMy code is experincing minor issue where the text isn't in the proper place, and to ensure that the frequency cutoff is at the right place. My code: % Define frequency range for the plot f = logspace(1, 5, 500); % Frequency range from 10 Hz to 100 kHz w = 2 * pi * f; % Angular frequency % Parameters for the filters - let's adjust these to get more reasonable cutoffs R = 1e3; % Resistance in ohms (1 kΩ) C = 1e-6; % Capacitance in farads (1 μF) % For bandpass, we need appropriate L value for desired cutoffs L = 0.1; % Inductance in henries - adjusted for better bandpass response % Calculate cutoff frequencies first to verify they're in desired range f_cutoff_RC = 1 / (2 * pi * R * C); f_resonance = 1 / (2 * pi * sqrt(L * C)); Q_factor = (1/R) * sqrt(L/C); f_lower_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) + 1/(2*Q_factor)); f_upper_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) - 1/(2*Q_factor)); % Transfer functions % Low-pass filter (RC) H_low = 1 ./ (1 + 1i * w *…arrow_forwardI would like to know the main features about the following three concepts: 1. Default forwarded 2. WINS Server 3. IP Security (IPSec).arrow_forward
- map the following ER diagram into a relational database schema diagram. you should take into account all the constraints in the ER diagram. Underline the primary key of each relation, and show each foreign key as a directed arrow from the referencing attributes (s) to the referenced relation. NOTE: Need relational database schema diagramarrow_forwardWhat is business intelligence? Share the Business intelligence (BI) tools you have used and explain what types of decisions you made.arrow_forwardI need help fixing the minor issue where the text isn't in the proper place, and to ensure that the frequency cutoff is at the right place. My code: % Define frequency range for the plot f = logspace(1, 5, 500); % Frequency range from 10 Hz to 100 kHz w = 2 * pi * f; % Angular frequency % Parameters for the filters - let's adjust these to get more reasonable cutoffs R = 1e3; % Resistance in ohms (1 kΩ) C = 1e-6; % Capacitance in farads (1 μF) % For bandpass, we need appropriate L value for desired cutoffs L = 0.1; % Inductance in henries - adjusted for better bandpass response % Calculate cutoff frequencies first to verify they're in desired range f_cutoff_RC = 1 / (2 * pi * R * C); f_resonance = 1 / (2 * pi * sqrt(L * C)); Q_factor = (1/R) * sqrt(L/C); f_lower_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) + 1/(2*Q_factor)); f_upper_cutoff = f_resonance / (sqrt(1 + 1/(4*Q_factor^2)) - 1/(2*Q_factor)); % Transfer functions % Low-pass filter (RC) H_low = 1 ./ (1 + 1i * w *…arrow_forward
- Task 3. i) Compare your results from Tasks 1 and 2. j) Repeat Tasks 1 and 2 for 500 and 5,000 elements. k) Summarize run-time results in the following table: Time/size n String StringBuilder 50 500 5,000arrow_forwardCan you please solve this without AIarrow_forward1. Create a Vehicle.java file. Implement the public Vehicle and Car classes in Vehicle.java, including all the variables and methods in the UMLS. Vehicle - make: String model: String -year: int + Vehicle(String make, String, model, int, year) + getMake(): String + setMake(String make): void + getModel(): String + setModel(String model): void + getYear(): int + set Year(int year): void +toString(): String Car - numDoors: int + numberOfCar: int + Car(String make, String, model, int, year, int numDoors) + getNumDoors(): int + setNumDoors (int num Doors): void + toString(): String 2. Create a CarTest.java file. Implement a public CarTest class with a main method. In the main method, create one Car object and print the object using System.out.println(). Then, print the numberOfCar. Your printing result must follow the example output: make Toyota, model=Camry, year=2022 numDoors=4 1 Hint: You need to modify the toString methods in the Car class and Vehicle class!arrow_forward
- CHATGPT GAVE ME WRONG ANSWER PLEASE HELParrow_forwardHELP CHAT GPT GAVE ME WRONG ANSWER Consider the following implementation of a container that will be used in a concurrent environment. The container is supposed to be used like an indexed array, but provide thread-safe access to elements. struct concurrent_container { // Assume it’s called for any new instance soon before it’s ever used void concurrent_container() { init_mutex(&lock); } ~concurrent_container() { destroy_mutex(&lock); } // Returns element by its index. int get(int index) { lock.acquire(); if (index < 0 || index >= size) { return -1; } int result = data[index]; lock.release(); return result; } // Sets element by its index. void set(int index, int value) { lock.acquire(); if (index < 0 || index >= size) { resize(size); } data[index] = value; lock.release(); } // Extend maximum capacity of the…arrow_forwardWrite a C program using embedded assembler in which you use your own function to multiply by two without using the product. Tip: Just remember that multiplying by two in binary means shifting the number one place to the left. You can use the sample program from the previous exercise as a basis, which increments a variable. Just replace the INC instruction with SHL.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education