
MYPROGRAMMINGLAB WITH PEARSON ETEXT
8th Edition
ISBN: 9780134225340
Author: Deitel
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Concept explainers
Textbook Question
Chapter 3, Problem 3.24E
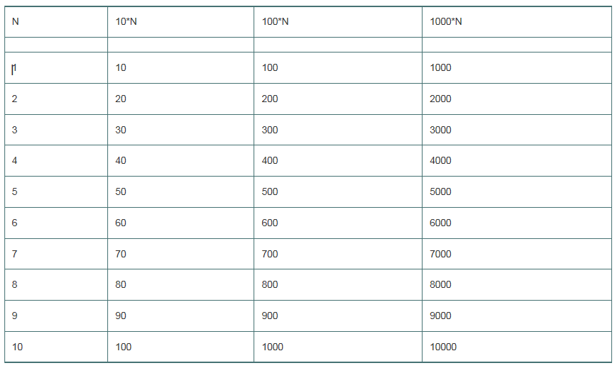
(Tabular Output) Write a
Expert Solution & Answer
Want to see the full answer?
Check out a sample textbook solution
Students have asked these similar questions
I need to define and discuss the uses of one monitoring or troubleshooting tool in Windows Server 2019. thank you
I would likr toget help with the following concepts:
- Windows Server features
- Windows Server versus Windows 10 used as a client-server network
I need to define and discuss the uses of one monitoring or troubleshooting tool in Windows Server 2019. thank you
Chapter 3 Solutions
MYPROGRAMMINGLAB WITH PEARSON ETEXT
Ch. 3 - Indentify and correct the errors in each of the...Ch. 3 - Fill in the blanks in each of the following: The...Ch. 3 - Prob. 3.12ECh. 3 - Write a single pseudocode statement that indicates...Ch. 3 - Formulate a pseudocode algorithm for each of the...Ch. 3 - State which of the following are true and which...Ch. 3 - For Exercises 3.16-3.20, perform each of these...Ch. 3 - For Exercises 3.16 -3.20, perform each of these...Ch. 3 - (Sales-Commission Calculator) One large chemical...Ch. 3 - (Interest Calculator) The simple interest on a...
Ch. 3 - (Salary Calculator) Develop a program that will...Ch. 3 - (Predecrementing vs. Postdecrementing)Write a...Ch. 3 - (Printing Numbers from a Loop) Write a program...Ch. 3 - (Find the Largest Number) The process of finding...Ch. 3 - (Tabular Output) Write a program that uses looping...Ch. 3 - (Tabular Output) Write a program that utilizes...Ch. 3 - (Find the Two Largest Numbers) Using an approach...Ch. 3 - (Validating User Input) Modify the program in...Ch. 3 - Prob. 3.28ECh. 3 - Prob. 3.29ECh. 3 - (Dangling-Else Problem) Determine the output for...Ch. 3 - (Another Dangling-Else Problem) Modify the...Ch. 3 - Prob. 3.32ECh. 3 - (Hollow Square of Asterisks) Modify the program...Ch. 3 - (Palindrome Tester) A palindrome is a number or a...Ch. 3 - (Printing the Decimal Equivalent of a Binary...Ch. 3 - (How Fast Is Your Computer?) How can you determine...Ch. 3 - (Detecting Multiples of 10) Write a program that...Ch. 3 - (Counting 7s) Write a program that reads an...Ch. 3 - (Checkerboard Pattern of Asterisks) Write a...Ch. 3 - (Multiples of 2 with an Infinite Loop) Write a...Ch. 3 - (Diameter, Circumference and Area of a Cirle)...Ch. 3 - Whats wrong with the following statement? Rewrite...Ch. 3 - (Sides of a Triangle) Write a program that reads...Ch. 3 - (Sides of a Right Triangle) Write a program that...Ch. 3 - (Factorial) The factorial of a nonnegative integer...Ch. 3 - (World-Population-Growth Calculator) Use the web...Ch. 3 - (Target-Heart-Rate Calculator) While exercising,...Ch. 3 - (Enforcing Privacy with Cryptography) The...
Additional Engineering Textbook Solutions
Find more solutions based on key concepts
How is the hydrodynamic entry length defined for flow in a pipe? Is the entry length longer in laminar or turbu...
Fluid Mechanics: Fundamentals and Applications
This optional Google account security feature sends you a message with a code that you must enter, in addition ...
SURVEY OF OPERATING SYSTEMS
How does a computers main memory differ from its auxiliary memory?
Java: An Introduction to Problem Solving and Programming (8th Edition)
What is an uninitialized variable?
Starting Out with Programming Logic and Design (5th Edition) (What's New in Computer Science)
1.2 Explain the difference between geodetic and plane
surveys,
Elementary Surveying: An Introduction To Geomatics (15th Edition)
Which of the following are illegal variable names in Python, and why? x 99bottles july2009 theSalesFigureForFis...
Starting Out with Python (4th Edition)
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Please solve and answer the questions correctly please. Thank you!!arrow_forwardConsidering the TM example of binary sum ( see attached)do the step-by-step of execution for the binary numbers 1101 and 11. Feel free to use the Formal Language Editor Tool to execute it; Write it down the current state of the tape (including the head position) and indicate the current state of the TM at each step.arrow_forwardI need help on inculding additonal code where I can can do the opposite code of MatLab, where the function of t that I enter becomes the result of F(t), in other words, turning the time-domain f(t) into the frequency-domain function F(s):arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr
C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning,
Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning, EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENTNp Ms Office 365/Excel 2016 I NtermedComputer ScienceISBN:9781337508841Author:CareyPublisher:Cengage
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENTNp Ms Office 365/Excel 2016 I NtermedComputer ScienceISBN:9781337508841Author:CareyPublisher:Cengage Programming with Microsoft Visual Basic 2017Computer ScienceISBN:9781337102124Author:Diane ZakPublisher:Cengage Learning
Programming with Microsoft Visual Basic 2017Computer ScienceISBN:9781337102124Author:Diane ZakPublisher:Cengage Learning

C++ Programming: From Problem Analysis to Program...
Computer Science
ISBN:9781337102087
Author:D. S. Malik
Publisher:Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:9781133187844
Author:Bronson, Gary J.
Publisher:Course Technology Ptr

Microsoft Visual C#
Computer Science
ISBN:9781337102100
Author:Joyce, Farrell.
Publisher:Cengage Learning,

EBK JAVA PROGRAMMING
Computer Science
ISBN:9781337671385
Author:FARRELL
Publisher:CENGAGE LEARNING - CONSIGNMENT

Np Ms Office 365/Excel 2016 I Ntermed
Computer Science
ISBN:9781337508841
Author:Carey
Publisher:Cengage

Programming with Microsoft Visual Basic 2017
Computer Science
ISBN:9781337102124
Author:Diane Zak
Publisher:Cengage Learning
Literals in Java Programming; Author: Sudhakar Atchala;https://www.youtube.com/watch?v=PuEU4S4B7JQ;License: Standard YouTube License, CC-BY
Type of literals in Python | Python Tutorial -6; Author: Lovejot Bhardwaj;https://www.youtube.com/watch?v=bwer3E9hj8Q;License: Standard Youtube License