
C How To Program, Global Edition
8th Edition
ISBN: 9781292110974
Author: Paul Deitel, Harvey Deitel
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Concept explainers
Textbook Question
Chapter 6, Problem 6.27E
(Eight Queens: Brute-Force Approaches) In this problem you’ll develop several brute-force approaches to solving the Eight Queens problem introduced in Exercise 6.26.
- Solve the Eight Queens problem, using the random brute-force technique developed in Exercise 6.25.
- Use an exhaustive technique (i.e., try all possible combinations of eight queens on the chessboard).
- Why do you suppose the exhaustive brute-force approach may not be appropriate for solving the Eight Queens problem?
- Compare and contrast the random brute-force and exhaustive brute-force approaches in general.
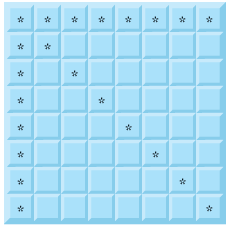
Fig. 6.27 The 22 squares eliminated by placing a queen in the upper-left corner.
Expert Solution & Answer
Want to see the full answer?
Check out a sample textbook solution
Students have asked these similar questions
THIS IS NOT A GRADING ASSIGNMENT:
Please only do lab 2.2 (bottom part of the first picture)
For that Lab 2.2 do:
*Part 1
*Part 2
*Part 3
I also attached Section 2.5.2 which is part of the step 1 so you can read what is it about.
Thank you!
can you please give me:
* the code (step 3)
*the list file (step 5)
*and answer step 6
Thank you
# Find the error# Why will the following code not print out a list of contact namesphoneBook = {'Doe, Jane' : '843-000-0000' ,'Doe, John' : '843-111-1111' ,'Smith, Adam' : '843-222-2222' ,'Jobs, Steve' : '999-333-3333' ,}for contact in phoneBook.values():print(contact)
Chapter 6 Solutions
C How To Program, Global Edition
Ch. 6 - Fill in the blanks in each of the following: C...Ch. 6 - State which of the following are true and which...Ch. 6 - Write statements to accomplish each of the...Ch. 6 - Consider a 2-by-5 integer array t. Write a...Ch. 6 - (Sales Commissions) Use a one-dimensional array to...Ch. 6 - (Bubble Sort) The bubble sort presented in Fig....Ch. 6 - Write loops that perform each of the following...Ch. 6 - Prob. 6.13ECh. 6 - (Mean, Median and Mode Program Modifications)...Ch. 6 - (Duplicate Elimination) Use a one-dimensional...
Ch. 6 - Label the elements of 3-by-5 two-dimensional array...Ch. 6 - What does the following program do?Ch. 6 - What does the following program do?Ch. 6 - (Dice Rolling) Write a program that simulates the...Ch. 6 - (Game of Craps) Write a program that runs 1000...Ch. 6 - Prob. 6.21ECh. 6 - (Total Sales) Use a two-dimensional array to solve...Ch. 6 - (Turtle Graphics) The Logo language made the...Ch. 6 - Prob. 6.24ECh. 6 - (Knights Tour: Brute-Force Approaches) In Exercise...Ch. 6 - (Eight Queens) Another puzzler for chess buffs is...Ch. 6 - (Eight Queens: Brute-Force Approaches) In this...Ch. 6 - (Duplicate Elimination) In Chapter 12, we explore...Ch. 6 - (Knights Tour: Closed Tour Test) In the Knights...Ch. 6 - (The Sieve of Eratosthenes) A prime integer is any...Ch. 6 - Prob. 6.31RECh. 6 - (Linear Search) Modify the program of Fig. 6.18 to...Ch. 6 - (Binary Search) Modify the program of Fig. 6.19 to...Ch. 6 - Prob. 6.35RECh. 6 - Prob. 6.36RECh. 6 - Prob. 6.37RE
Additional Engineering Textbook Solutions
Find more solutions based on key concepts
Explain how each of the following types of integrity constraints is enforced in the SQL CREATE TABLE commands: ...
Modern Database Management
What is the purpose of an objects sizing handles?
Starting Out With Visual Basic (8th Edition)
Describe the three steps that must be taken when a file is used by a program.
Starting Out with Python (4th Edition)
What is the purpose of the let constructs in functional languages?
Concepts Of Programming Languages
(Instance Variables) Explain the purpose of an instance variable.
Java How to Program, Early Objects (11th Edition) (Deitel: How to Program)
Suppose the variable X in a program was declared to be of type integer. What error would occur when executing t...
Computer Science: An Overview (13th Edition) (What's New in Computer Science)
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- # Find the error:# The following code creates an empty dictionary and attempts to add a record# Why will the following code not create a new dictionary entry as intended?phoneBook = {}phoneBook{'Jobs, Steve'} = '999-111-1111'arrow_forwardSelect all the possible polar representations of the vector that is obtained from rotating where by Zrot Ź x = 3e² T= 3п 8 Hint: Consider the negative angle that is equivalent to the positive angle of the rotated vector. 0arrow_forwardCharacter Analysis If you have downloaded the source code you will find a file named text.txt on the Chapter 08 folder. Write a program that reads the file's contents and determines the following: The number of uppercase letters in the file The number of lowercase letter in the file The number of digits in the file The number of whitespace characters in the filearrow_forward
- Write a program that reads the text file's contents and calculates and outputs the following in this order: • The number of words in the file • The number of lines in the file • The number of uppercase letters in the file • The number of lowercase letters in the file • The number of digits in the file • The number of letter H's in the file • The number of whitespace characters in the file NOTE: Your program should include at least one try-except error handling statement block. Your program should also validate any input that could cause your program to crash. I'm Henery The Eighth, I Am! Henery The Eighth, I Am, I am!I got married to the widow next door,She's been married seven times before.And ev'ryone was a Henery,She wouldn't have Willie or a Sam.I'm her eighth old man named Henery,Henery the Eighth, I Am!Second verse same as the first!I'm Henery The Eighth, I Am! Henery The Eighth, I Am, I am!I got married to the widow next door,She's been married seven times before.And…arrow_forwardFigure 4-40 Modern Database Management, 13th edition, question 4-53arrow_forwardWhich of the following needs improvement in the dashboard shown? A. Instructional clarity missing for the views B. Filter placed at the top of the dashboard C. Inconsistent use of colors to represent missed goals D. Dashboard title too largearrow_forward
- If we click Show dashboard title in this dashboard, what will the title be?arrow_forwardPlease draw the diagram where it is asked to be drawn. Don't just describe how to do it.arrow_forwardC. Homework Assignment Task: Write a one-page CV using the provided template. Steps: 1. Use the CV guide to structure your CV. 2. Fill in each section with real information about yourself. 3. Format your CV neatly and use professional language. 4. Submit to the instructor before the next classarrow_forward
- Simulate on a vertical time axis (with events labeled with the senders names A-D) the contention period of FOUR equally distanced Ethernet stations that all attempt to transmit at T=0 a minimally sized frame, in the style of the binary Exponential Backoff Algorithm. Assume that time is measured in slot times, and that exactly one slot time is needed to detect a collision (so that if two stations transmit at T=1 and collide, and one of them chooses a backoff time k=0, then that station will transmit again at T=2). Use as coin flip (source of randomness) an ID written in binary. use the bits in order from the least significant to the most significant. If for a given coin throw you need k bits, use the least significant ID bit extracted in the corresponding group of bits, as the least significant bit of the coin thrown. Start be writing the ID, which is 904012207 As example of the expected answer format, with the random sequence R: 100101010101001011001010 01 01011 10010 1010 1010 010…arrow_forwardBig State University The Big State University course catalog reads as follows: "To enroll in MIS 260, which is an advanced course, a student must complete two prerequisites: MIS 120 and MIS 222. A student who completes either one of these prerequisites and obtains the instructor's permission, however, will be allowed to take MIS 260." Tasks 1. Create a decision table that describes the Big State University course catalog regarding eligibility for MIS 260. Show all possible rules. 2. Simplify the table you just created. Describe the results. 3. Draw a simplified decision tree to represent the Big State University catalog. Describe the results. 4. Why might you use a decision tree rather than a decision table?arrow_forwardWhat is the ALU result if the 4-bit ALU Control signal is 0100? What happens if the ALU Control signal is 0101?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology PtrProgramming Logic & Design ComprehensiveComputer ScienceISBN:9781337669405Author:FARRELLPublisher:Cengage
C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology PtrProgramming Logic & Design ComprehensiveComputer ScienceISBN:9781337669405Author:FARRELLPublisher:Cengage Operations Research : Applications and AlgorithmsComputer ScienceISBN:9780534380588Author:Wayne L. WinstonPublisher:Brooks Cole
Operations Research : Applications and AlgorithmsComputer ScienceISBN:9780534380588Author:Wayne L. WinstonPublisher:Brooks Cole Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning,
Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning, EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT

C++ Programming: From Problem Analysis to Program...
Computer Science
ISBN:9781337102087
Author:D. S. Malik
Publisher:Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:9781133187844
Author:Bronson, Gary J.
Publisher:Course Technology Ptr

Programming Logic & Design Comprehensive
Computer Science
ISBN:9781337669405
Author:FARRELL
Publisher:Cengage

Operations Research : Applications and Algorithms
Computer Science
ISBN:9780534380588
Author:Wayne L. Winston
Publisher:Brooks Cole

Microsoft Visual C#
Computer Science
ISBN:9781337102100
Author:Joyce, Farrell.
Publisher:Cengage Learning,

EBK JAVA PROGRAMMING
Computer Science
ISBN:9781337671385
Author:FARRELL
Publisher:CENGAGE LEARNING - CONSIGNMENT
Python Tutorial #10; Math Functions in Python; Author: Art of Engineer;https://www.youtube.com/watch?v=OviXsGf4qmY;License: Standard YouTube License, CC-BY