
C How To Program, Global Edition
8th Edition
ISBN: 9781292110974
Author: Paul Deitel, Harvey Deitel
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Concept explainers
Textbook Question
Chapter 6, Problem 6.17E
What does the following
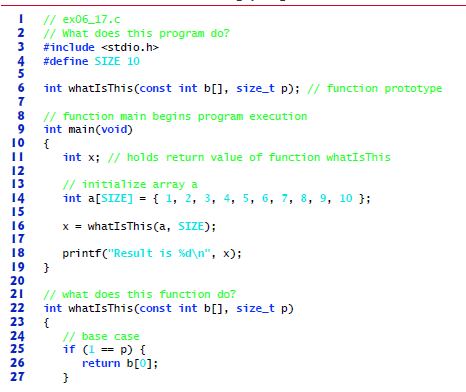
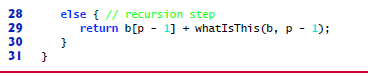
Expert Solution & Answer
Trending nowThis is a popular solution!
Learn your wayIncludes step-by-step video

schedule04:17
Students have asked these similar questions
Solve in MATLAB
Hello please look at the attached picture. I need an detailed explanation of the architecture
Information Security Risk and Vulnerability Assessment
1- Which TCP/IP protocol is used to convert the IP address to the Mac address? Explain 2-What popular switch feature allows you to create communication boundaries between systems connected to the switch3- what types of vulnerability directly related to the programmer of the software?4- Who ensures the entity implements appropriate security controls to protect an asset?
Please do not use AI and add refrence
Chapter 6 Solutions
C How To Program, Global Edition
Ch. 6 - Fill in the blanks in each of the following: C...Ch. 6 - State which of the following are true and which...Ch. 6 - Write statements to accomplish each of the...Ch. 6 - Consider a 2-by-5 integer array t. Write a...Ch. 6 - (Sales Commissions) Use a one-dimensional array to...Ch. 6 - (Bubble Sort) The bubble sort presented in Fig....Ch. 6 - Write loops that perform each of the following...Ch. 6 - Prob. 6.13ECh. 6 - (Mean, Median and Mode Program Modifications)...Ch. 6 - (Duplicate Elimination) Use a one-dimensional...
Ch. 6 - Label the elements of 3-by-5 two-dimensional array...Ch. 6 - What does the following program do?Ch. 6 - What does the following program do?Ch. 6 - (Dice Rolling) Write a program that simulates the...Ch. 6 - (Game of Craps) Write a program that runs 1000...Ch. 6 - Prob. 6.21ECh. 6 - (Total Sales) Use a two-dimensional array to solve...Ch. 6 - (Turtle Graphics) The Logo language made the...Ch. 6 - Prob. 6.24ECh. 6 - (Knights Tour: Brute-Force Approaches) In Exercise...Ch. 6 - (Eight Queens) Another puzzler for chess buffs is...Ch. 6 - (Eight Queens: Brute-Force Approaches) In this...Ch. 6 - (Duplicate Elimination) In Chapter 12, we explore...Ch. 6 - (Knights Tour: Closed Tour Test) In the Knights...Ch. 6 - (The Sieve of Eratosthenes) A prime integer is any...Ch. 6 - Prob. 6.31RECh. 6 - (Linear Search) Modify the program of Fig. 6.18 to...Ch. 6 - (Binary Search) Modify the program of Fig. 6.19 to...Ch. 6 - Prob. 6.35RECh. 6 - Prob. 6.36RECh. 6 - Prob. 6.37RE
Additional Engineering Textbook Solutions
Find more solutions based on key concepts
Describe a method that can be used to gather a piece of data such as the users age.
Web Development and Design Foundations with HTML5 (8th Edition)
Write the statement that calls a superclass constructor and passes the arguments x, y, and z.
Starting Out with Java: From Control Structures through Data Structures (4th Edition) (What's New in Computer Science)
Suppose a computer manufacturer develops a new machine architecture. To what extent should the company be allow...
Computer Science: An Overview (13th Edition) (What's New in Computer Science)
In each case, determine the internal bending moment as a function of x, and state the necessary boundary and/or...
Mechanics of Materials (10th Edition)
Present Value Suppose you want to deposit a certain amount of money into a savings account and then leave it al...
Starting Out with C++ from Control Structures to Objects (9th Edition)
For the circuit shown, find (a) the voltage υ, (b) the power delivered to the circuit by the current source, an...
Electric Circuits. (11th Edition)
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Could you help me to know features of the following concepts: - commercial CA - memory integrity - WMI filterarrow_forwardBriefly describe the issues involved in using ATM technology in Local Area Networksarrow_forwardFor this question you will perform two levels of quicksort on an array containing these numbers: 59 41 61 73 43 57 50 13 96 88 42 77 27 95 32 89 In the first blank, enter the array contents after the top level partition. In the second blank, enter the array contents after one more partition of the left-hand subarray resulting from the first partition. In the third blank, enter the array contents after one more partition of the right-hand subarray resulting from the first partition. Print the numbers with a single space between them. Use the algorithm we covered in class, in which the first element of the subarray is the partition value. Question 1 options: Blank # 1 Blank # 2 Blank # 3arrow_forward
- 1. Transform the E-R diagram into a set of relations. Country_of Agent ID Agent H Holds Is_Reponsible_for Consignment Number $ Value May Contain Consignment Transports Container Destination Ф R Goes Off Container Number Size Vessel Voyage Registry Vessel ID Voyage_ID Tonnagearrow_forwardI want to solve 13.2 using matlab please helparrow_forwarda) Show a possible trace of the OSPF algorithm for computing the routing table in Router 2 forthis network.b) Show the messages used by RIP to compute routing tables.arrow_forward
- using r language to answer question 4 Question 4: Obtain a 95% standard normal bootstrap confidence interval, a 95% basic bootstrap confidence interval, and a percentile confidence interval for the ρb12 in Question 3.arrow_forwardusing r language to answer question 4. Question 4: Obtain a 95% standard normal bootstrap confidence interval, a 95% basic bootstrap confidence interval, and a percentile confidence interval for the ρb12 in Question 3.arrow_forwardusing r languagearrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning,
Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning, C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr
C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr

C++ Programming: From Problem Analysis to Program...
Computer Science
ISBN:9781337102087
Author:D. S. Malik
Publisher:Cengage Learning

Microsoft Visual C#
Computer Science
ISBN:9781337102100
Author:Joyce, Farrell.
Publisher:Cengage Learning,

C++ for Engineers and Scientists
Computer Science
ISBN:9781133187844
Author:Bronson, Gary J.
Publisher:Course Technology Ptr