
Suppose that m is a positive integer with m>2 An m-ary Huffman code for a set of N symbols can be constructed analogously to the construction of a binary Huffman code. At the initial step, ((N - 1) mod (m - 1)) + 1 trees consisting of a single vertex with least weights are combined into a rooted tree with these vertices as leaves. At each subsequent step, the m trees of least weight are combined into an m-ary tree.
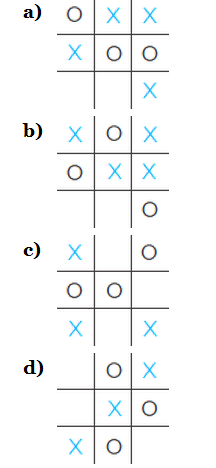
37. Draw the subtree of the game tree for tic-tac--toe beginning at each of these positions. Determine the value of each of these subtre.es.
Want to see the full answer?
Check out a sample textbook solution
Chapter 11 Solutions
DISCRETE MATHEMATICS+ITS APPL. (LL)-W/A
Additional Math Textbook Solutions
Finite Mathematics for Business, Economics, Life Sciences and Social Sciences
Pathways To Math Literacy (looseleaf)
College Algebra Essentials (5th Edition)
APPLIED STAT.IN BUS.+ECONOMICS
Precalculus: A Unit Circle Approach (3rd Edition)
- Negate the following compound statement using De Morgans's laws.arrow_forwardQuestion 6: Negate the following compound statements, using De Morgan's laws. A) If Alberta was under water entirely then there should be no fossil of mammals.arrow_forwardNegate the following compound statement using De Morgans's laws.arrow_forward
- 18.10. Let f be analytic inside and on the unit circle 7. Show that, for 0<|z|< 1, f(E) f(E) 2πif(z) = --- d.arrow_forwardCharacterize (with proof) all connected graphs that contain no even cycles in terms oftheir blocks.arrow_forward18.4. Let f be analytic within and on a positively oriented closed contoury, and the point zo is not on y. Show that L f(z) (-20)2 dz = '(2) dz. 2-20arrow_forward
- 18.9. Let denote the boundary of the rectangle whose vertices are -2-2i, 2-21,2+i and -2+i in the positive direction. Evaluate each of the following integrals: (a). rdz, (b). dz (b). COS 2 coz dz, (z+1) (d). 之一 z 2 +2 dz, (e). dz (c). (2z + 1)2dz, (2z+1) 1 (f). £, · [e² sin = + (2² + 3)²] dz. z (22+3)2arrow_forwardLet G be a connected graph that does not have P4 or C3 as an induced subgraph (i.e.,G is P4, C3 free). Prove that G is a complete bipartite grapharrow_forward18.8. (a). Let be the contour z = e-≤0≤ traversed in the า -dz = 2xi. positive direction. Show that, for any real constant a, Lex dzarrow_forward
- Prove sufficiency of the condition for a graph to be bipartite that is, prove that if G hasno odd cycles then G is bipartite as follows:Assume that the statement is false and that G is an edge minimal counterexample. That is, Gsatisfies the conditions and is not bipartite but G − e is bipartite for any edge e. (Note thatthis is essentially induction, just using different terminology.) What does minimality say aboutconnectivity of G? Can G − e be disconnected? Explain why if there is an edge between twovertices in the same part of a bipartition of G − e then there is an odd cyclearrow_forwardLet G be a connected graph that does not have P4 or C4 as an induced subgraph (i.e.,G is P4, C4 free). Prove that G has a vertex adjacent to all othersarrow_forwardf(z) 18.7. Let f(z) = (e² + e³)/2. Evaluate dz, where y is any simple closed curve enclosing 0.arrow_forward
 Elements Of Modern AlgebraAlgebraISBN:9781285463230Author:Gilbert, Linda, JimmiePublisher:Cengage Learning,
Elements Of Modern AlgebraAlgebraISBN:9781285463230Author:Gilbert, Linda, JimmiePublisher:Cengage Learning, Linear Algebra: A Modern IntroductionAlgebraISBN:9781285463247Author:David PoolePublisher:Cengage Learning
Linear Algebra: A Modern IntroductionAlgebraISBN:9781285463247Author:David PoolePublisher:Cengage Learning

