
DATABASE SYSTEMS
13th Edition
ISBN: 9780357095607
Author: Coronel
Publisher: CENGAGE L
expand_more
expand_more
format_list_bulleted
Concept explainers
Expert Solution & Answer
thumb_up100%
Chapter 4, Problem 1RQ
Explanation of Solution
Conditions:
Following are the conditions should be met before an entity is referred as a weak entity:
- The entity should be “existence-dependent” on its parent entity.
- If an entity is referred as an “existence-dependent”, then that entity can exist in the
database if and only if when it is related with another entity existence.
- If an entity is referred as an “existence-dependent”, then that entity can exist in the
- The entity should inherits a section of its primary key (PK) from its parent entity.
Example:
Consider the following ER diagram along with its attributes:
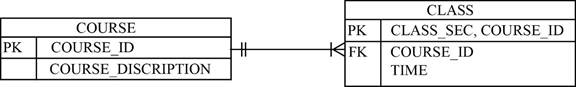
Explanation:
- The entity CLASS is “existence-dependent” on COURSE entity. Hence the CLASS entity uses a PK component from its parent entity (COURSE).
- The CLASS entity’s PK is (COURSE_ID, CLASS_SEC).
- In this strong implementation, the CLASS entity is referred as a weak entity between COURSE and CLASS.
Want to see more full solutions like this?
Subscribe now to access step-by-step solutions to millions of textbook problems written by subject matter experts!
Students have asked these similar questions
"Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."
| √ (r² + r + 1)e^ dr
Ensure you answer the question asked at the end of the document. Do not just paste things without the GNS3 console outputs
Chapter 4 Solutions
DATABASE SYSTEMS
Ch. 4 - Prob. 1RQCh. 4 - What is a strong (or identifying) relationship,...Ch. 4 - Prob. 4RQCh. 4 - Suppose you are working within the framework of...Ch. 4 - Prob. 6RQCh. 4 - Prob. 7RQCh. 4 - Discuss the difference between a composite key and...Ch. 4 - What two courses of action are available to a...Ch. 4 - What is a derived attribute? Give an example. What...Ch. 4 - Prob. 11RQ
Ch. 4 - Discuss two ways in which the 1:M relationship...Ch. 4 - Prob. 13RQCh. 4 - Prob. 14RQCh. 4 - Briefly, but precisely, explain the difference...Ch. 4 - What are multivalued attributes, and how can they...Ch. 4 - Prob. 17RQCh. 4 - Prob. 18RQCh. 4 - What two attributes must be contained in the...Ch. 4 - Describe precisely the composition of the...Ch. 4 - Prob. 21RQCh. 4 - Prob. 1PCh. 4 - Create a complete ERD in Crows Foot notation that...Ch. 4 - Prob. 4PCh. 4 - Prob. 5PCh. 4 - Prob. 6PCh. 4 - Prob. 7PCh. 4 - Prob. 8PCh. 4 - Prob. 9PCh. 4 - Prob. 10PCh. 4 - Prob. 11C
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward"Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward"Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward
- "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forwardSolve this "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward"Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward
- "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forwardSpecifications: Part-1Part-1: DescriptionIn this part of the lab you will build a single operation ALU. This ALU will implement a bitwise left rotation. Forthis lab assignment you are not allowed to use Digital's Arithmetic components.IF YOU ARE FOUND USING THEM, YOU WILL RECEIVE A ZERO FOR LAB2!The ALU you will be implementing consists of two 4-bit inputs (named inA and inB) and one 4-bit output (named out). Your ALU must rotate the bits in inA by the amount given by inB (i.e. 0-15).Part-1: User InterfaceYou are provided an interface file lab2_part1.dig; start Part-1 from this file.NOTE: You are not permitted to edit the content inside the dotted lines rectangle. Part-1: ExampleIn the figure above, the input values that we have selected to test are inA = {inA_3, inA_2, inA_1, inA_0} = {0, 1, 0,0} and inB = {inB_3, inB_2, inB_1, inB_0} = {0, 0, 1, 0}. Therefore, we must rotate the bus 0100 bitwise left by00102, or 2 in base 10, to get {0, 0, 0, 1}. Please note that a rotation left is…arrow_forwardSolve this "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward
- Solve this "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward"Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forwardSolve this "Do not use AI tools. Solve the problem by hand on paper only and upload a photo of your handwritten solution."arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781305627482Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781305627482Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
 Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781285196145Author:Steven, Steven Morris, Carlos Coronel, Carlos, Coronel, Carlos; Morris, Carlos Coronel and Steven Morris, Carlos Coronel; Steven Morris, Steven Morris; Carlos CoronelPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781285196145Author:Steven, Steven Morris, Carlos Coronel, Carlos, Coronel, Carlos; Morris, Carlos Coronel and Steven Morris, Carlos Coronel; Steven Morris, Steven Morris; Carlos CoronelPublisher:Cengage Learning Principles of Information Systems (MindTap Course...Computer ScienceISBN:9781285867168Author:Ralph Stair, George ReynoldsPublisher:Cengage Learning
Principles of Information Systems (MindTap Course...Computer ScienceISBN:9781285867168Author:Ralph Stair, George ReynoldsPublisher:Cengage Learning Fundamentals of Information SystemsComputer ScienceISBN:9781305082168Author:Ralph Stair, George ReynoldsPublisher:Cengage Learning
Fundamentals of Information SystemsComputer ScienceISBN:9781305082168Author:Ralph Stair, George ReynoldsPublisher:Cengage Learning

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781305627482
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning


Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781285196145
Author:Steven, Steven Morris, Carlos Coronel, Carlos, Coronel, Carlos; Morris, Carlos Coronel and Steven Morris, Carlos Coronel; Steven Morris, Steven Morris; Carlos Coronel
Publisher:Cengage Learning

Principles of Information Systems (MindTap Course...
Computer Science
ISBN:9781285867168
Author:Ralph Stair, George Reynolds
Publisher:Cengage Learning

Fundamentals of Information Systems
Computer Science
ISBN:9781305082168
Author:Ralph Stair, George Reynolds
Publisher:Cengage Learning