
Introduction to Java Programming and Data Structures, Comprehensive Version (11th Edition)
11th Edition
ISBN: 9780134670942
Author: Y. Daniel Liang
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Concept explainers
Textbook Question
Chapter 3.6, Problem 3.6.1CP
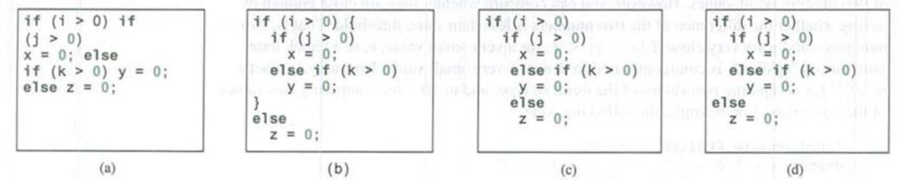
Which of the following statements are equivalent? Which ones are correctly indented?
Expert Solution & Answer
Want to see the full answer?
Check out a sample textbook solution
Students have asked these similar questions
Write the SQL code that permits to implement the tables: Student and Transcript. NB: Add the constraints on the attributes – keys and other.
Draw an ERD that will involve the entity types: Professor, Student, Department and Course. Be sure to add relationship types, key attributes, attributes and multiplicity on the ERD.
Draw an ERD that represents a book in a library system. Be sure to add relationship types, key attributes, attributes and multiplicity on the ERD.
Chapter 3 Solutions
Introduction to Java Programming and Data Structures, Comprehensive Version (11th Edition)
Ch. 3.2 - List six relational operators.Ch. 3.2 - Assuming x is 1, show the result of the following...Ch. 3.2 - Can the following conversions involving casting be...Ch. 3.3 - Write an if statement that assigns 1 to x if y is...Ch. 3.3 - Write an if statement that increases pay by 3% if...Ch. 3.3 - Prob. 3.3.3CPCh. 3.4 - Write an if statement that increases pay by 3% if...Ch. 3.4 - What is the output of the code in (a) and (b) if...Ch. 3.5 - Prob. 3.5.1CPCh. 3.5 - Suppose x = 2andy = 3. Show the output, if any, of...
Ch. 3.5 - What is wrong in the following code? if (score =...Ch. 3.6 - Which of the following statements are equivalent?...Ch. 3.6 - Prob. 3.6.2CPCh. 3.6 - Are the following statements correct? Which one is...Ch. 3.6 - Prob. 3.6.4CPCh. 3.7 - Prob. 3.7.1CPCh. 3.7 - a. How do you generate a random integer i such...Ch. 3.9 - Are the following two statements equivalent?Ch. 3.10 - Assuming that x is 1, show the result of the...Ch. 3.10 - (a) Write a Boolean expression that evaluates to...Ch. 3.10 - (a) Write a Boolean expression for |x 5| 4.5....Ch. 3.10 - Assume x and y are int type. Which of the...Ch. 3.10 - Are the following two expressions the same? (a) x...Ch. 3.10 - What is the value of the expression x = 50 x =...Ch. 3.10 - Suppose, when you run the following program, you...Ch. 3.10 - Write a Boolean expression that evaluates to true...Ch. 3.10 - Write a Boolean expression that evaluates to true...Ch. 3.10 - Write a Boolean expression that evaluates to true...Ch. 3.10 - Write a Boolean expression that evaluates to true...Ch. 3.11 - Prob. 3.11.1CPCh. 3.12 - What happens if you enter an integer as 05?Ch. 3.13 - What data types are required for a switch...Ch. 3.13 - What is y after the following switch statement is...Ch. 3.13 - What is x after the following if-else statement is...Ch. 3.13 - Write a switch statement that displays Sunday,...Ch. 3.13 - Prob. 3.13.5CPCh. 3.14 - Suppose when you run the following program, you...Ch. 3.14 - Rewrite the following if statements using the...Ch. 3.14 - Rewrite the following codes using if-else...Ch. 3.14 - Write an expression using a conditional operator...Ch. 3.15 - List the precedence order of the Boolean...Ch. 3.15 - True or false? All the binary operators except =...Ch. 3.15 - Evaluate the following expressions: 2 2 3 2 4 ...Ch. 3.15 - Is (x 0 x 10) the same as ((x 0) (x 10))? Is...Ch. 3 - (Algebra: solve quadratic equations) The two roots...Ch. 3 - (Game: add three numbers) The program in Listing...Ch. 3 - (Algebra: solve 2 2 linear equations) A linear...Ch. 3 - (Random month) Write a program that randomly...Ch. 3 - (Find future dates) Write a program that prompts...Ch. 3 - (Health application: BMI) Revise Listing 3.4,...Ch. 3 - (Financial application: monetary units) Modify...Ch. 3 - Prob. 3.8PECh. 3 - (Business: check ISBN-10) An ISBN-10...Ch. 3 - (Game: addition quiz) Listing 3.3,...Ch. 3 - (Find the number of days in a month) Write a...Ch. 3 - (Palindrome integer) Write a program that prompts...Ch. 3 - (Financial application: compute taxes) Listing...Ch. 3 - (Game: heads or tails) Write a program that lets...Ch. 3 - (Game: lottery) Revise Listing 3.8, Lottery.java....Ch. 3 - Prob. 3.16PECh. 3 - (Game: scissor, rock, paper) Write a program that...Ch. 3 - (Cost of shipping) A shipping company uses the...Ch. 3 - (Compute the perimeter of a triangle) Write a...Ch. 3 - (Science: wind-chill temperature) Programming...Ch. 3 - Prob. 3.21PECh. 3 - (Geometry: point in a circle?) Write a program...Ch. 3 - (Geometry: point in a rectangle?) Write a program...Ch. 3 - (Game: pick a card) Write a program that simulates...Ch. 3 - (Geometry: intersecting point) Two points on line...Ch. 3 - (Use the , ||, and ^ operators) Write a program...Ch. 3 - (Geometry: points in triangle?) Suppose a right...Ch. 3 - (Geometry: two rectangles) Write a program that...Ch. 3 - (Geometry: two circles) Write a program that...Ch. 3 - (Current time) Revise Programming Exercise 2.8 to...Ch. 3 - (Financials: currency exchange) Write a program...Ch. 3 - Prob. 3.32PECh. 3 - (Financial: compare costs) Suppose you shop for...Ch. 3 - Prob. 3.34PE
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- 2:21 m Ο 21% AlmaNet WE ARE HIRING Experienced Freshers Salesforce Platform Developer APPLY NOW SEND YOUR CV: Email: hr.almanet@gmail.com Contact: +91 6264643660 Visit: www.almanet.in Locations: India, USA, UK, Vietnam (Remote & Hybrid Options Available)arrow_forwardProvide a detailed explanation of the architecture on the diagramarrow_forwardhello please explain the architecture in the diagram below. thanks youarrow_forward
- Complete the JavaScript function addPixels () to calculate the sum of pixelAmount and the given element's cssProperty value, and return the new "px" value. Ex: If helloElem's width is 150px, then calling addPixels (hello Elem, "width", 50) should return 150px + 50px = "200px". SHOW EXPECTED HTML JavaScript 1 function addPixels (element, cssProperty, pixelAmount) { 2 3 /* Your solution goes here *1 4 } 5 6 const helloElem = document.querySelector("# helloMessage"); 7 const newVal = addPixels (helloElem, "width", 50); 8 helloElem.style.setProperty("width", newVal); [arrow_forwardSolve in MATLABarrow_forwardHello please look at the attached picture. I need an detailed explanation of the architecturearrow_forward
- Information Security Risk and Vulnerability Assessment 1- Which TCP/IP protocol is used to convert the IP address to the Mac address? Explain 2-What popular switch feature allows you to create communication boundaries between systems connected to the switch3- what types of vulnerability directly related to the programmer of the software?4- Who ensures the entity implements appropriate security controls to protect an asset? Please do not use AI and add refrencearrow_forwardFind the voltage V0 across the 4K resistor using the mesh method or nodal analysis. Note: I have already simulated it and the value it should give is -1.714Varrow_forwardResolver por superposicionarrow_forward
- Describe three (3) Multiplexing techniques common for fiber optic linksarrow_forwardCould you help me to know features of the following concepts: - commercial CA - memory integrity - WMI filterarrow_forwardBriefly describe the issues involved in using ATM technology in Local Area Networksarrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning,
Microsoft Visual C#Computer ScienceISBN:9781337102100Author:Joyce, Farrell.Publisher:Cengage Learning, C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning
C++ Programming: From Problem Analysis to Program...Computer ScienceISBN:9781337102087Author:D. S. MalikPublisher:Cengage Learning C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr
C++ for Engineers and ScientistsComputer ScienceISBN:9781133187844Author:Bronson, Gary J.Publisher:Course Technology Ptr EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT
EBK JAVA PROGRAMMINGComputer ScienceISBN:9781337671385Author:FARRELLPublisher:CENGAGE LEARNING - CONSIGNMENT

Microsoft Visual C#
Computer Science
ISBN:9781337102100
Author:Joyce, Farrell.
Publisher:Cengage Learning,

C++ Programming: From Problem Analysis to Program...
Computer Science
ISBN:9781337102087
Author:D. S. Malik
Publisher:Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:9781133187844
Author:Bronson, Gary J.
Publisher:Course Technology Ptr

EBK JAVA PROGRAMMING
Computer Science
ISBN:9781337671385
Author:FARRELL
Publisher:CENGAGE LEARNING - CONSIGNMENT
Literals in Java Programming; Author: Sudhakar Atchala;https://www.youtube.com/watch?v=PuEU4S4B7JQ;License: Standard YouTube License, CC-BY
Type of literals in Python | Python Tutorial -6; Author: Lovejot Bhardwaj;https://www.youtube.com/watch?v=bwer3E9hj8Q;License: Standard Youtube License