
EBK NUMERICAL METHODS FOR ENGINEERS
7th Edition
ISBN: 9780100254145
Author: Chapra
Publisher: YUZU
expand_more
expand_more
format_list_bulleted
Textbook Question
Chapter 2, Problem 1P
Write pseudocode to implement the flowchart depicted in Fig. P2.1. Make sure that proper indentation is included to make the structure clear.
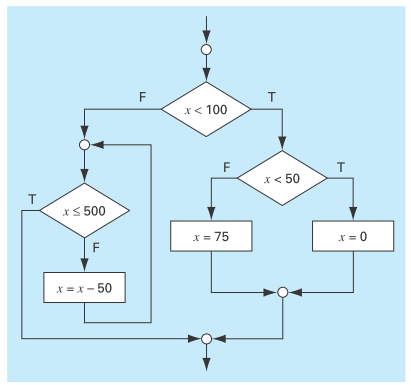
FIGURE P2.1
Expert Solution & Answer
To determine
The pseudo code for the flow chart provided flowchart.
Answer to Problem 1P
Solution:
The pseudo codeto the provided question is as follows:
IF x < 100 THEN
IF x < 50 THEN
x = 0
ELSE
x = 75
END IF
ELSE
DO
IF x <= 500 EXIT
x = x - 50
END DO
ENDIF
Explanation of Solution
Given:
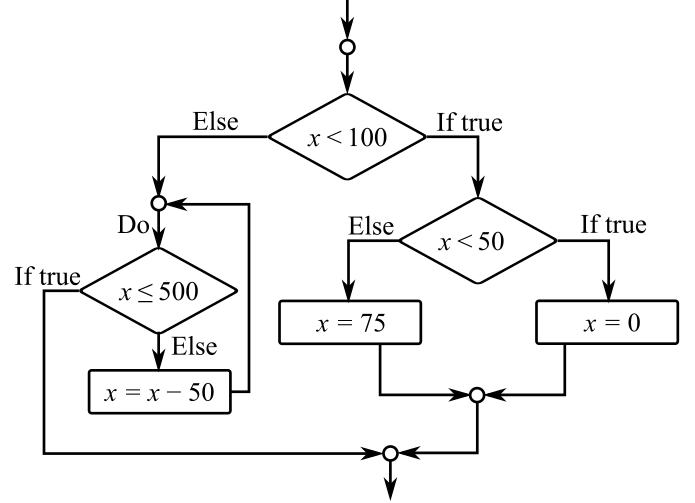
The flow chart is as follows:

The flow chart,

The pseudo code to the provided question is as follows:
IF x < 100 THEN
IF x < 50 THEN
x = 0
ELSE
x = 75
END IF
ELSE
DO
IF x <= 500 EXIT
x = x - 50
END DO
ENDIF
Want to see more full solutions like this?
Subscribe now to access step-by-step solutions to millions of textbook problems written by subject matter experts!
Students have asked these similar questions
Q4: Discuss the stability critical point of the ODES x + sin(x) = 0 and draw
phase portrait.
Using Karnaugh maps and Gray coding, reduce the following circuit represented as a table and write the final circuit in simplest form (first in terms of number of gates then in terms of fan-in of those gates). HINT: Pay closeattention to both the 1’s and the 0’s of the function.
Recall the RSA encryption/decryption system. The following questions are based on RSA. Suppose n (=15) is the product of the two prime numbers 3 and 5.1. Find an encryption key e for for the pair (e, n)2. Find a decryption key d for for the pair (d, n)3. Given the plaintext message x = 3, find the ciphertext y = x^(e) (where x^e is the message x encoded with encryption key e)4. Given the ciphertext message y (which you found in previous part), Show that the original message x = 3 can be recovered using (d, n)
Chapter 2 Solutions
EBK NUMERICAL METHODS FOR ENGINEERS
Ch. 2 - 2.1 Write pseudocode to implement the flowchart...Ch. 2 - Prob. 2PCh. 2 - 2.3 Develop, debug, and document a program to...Ch. 2 - The sine function can be evaluated by the...Ch. 2 - 2.5 Develop, debug, and document a program for...Ch. 2 - The following algorithm is designed to determine a...Ch. 2 - The divide and average method, an old-time method...Ch. 2 - 2.8 An amount of money P is invested in an account...Ch. 2 - 2.9 Economic formulas are available to compute...Ch. 2 - 2.10 The average daily temperature for an area can...
Ch. 2 - Develop, debug, and test a program in either a...Ch. 2 - 2.12 The bubble sort is an inefficient, but...Ch. 2 - Figure P2.13 shows a cylindrical tank with a...Ch. 2 - 2.14 Two distances are required to specify the...Ch. 2 - Develop a well-structured function procedure that...Ch. 2 - Prob. 16PCh. 2 - Develop well-structured programs to (a) determine...Ch. 2 - 2.18 Piecewise functions are sometimes useful when...Ch. 2 - Develop a well-structured function to determine...Ch. 2 - 2.20 Develop a well-structured function to...Ch. 2 - 2.21 Manning’s equation can be used to compute the...Ch. 2 - 2.22 A simply supported beam is loaded as shown in...Ch. 2 - ThevolumeV of liquid in ahollow horizontal...Ch. 2 - 2.24 Develop a well-structured program to compute...Ch. 2 - The pseudocode in Fig. P2.25 computes the...Ch. 2 - 2.26 The height of a small rocket y can be...Ch. 2 - 2.27 As depicted in Fig. P2.27, a water tank...
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, mechanical-engineering and related others by exploring similar questions and additional content below.Similar questions
- Theorem 1: A number n ∈ N is divisible by 3 if and only if when n is writtenin base 10 the sum of its digits is divisible by 3. As an example, 132 is divisible by 3 and 1 + 3 + 2 is divisible by 3.1. Prove Theorem 1 2. Using Theorem 1 construct an NFA over the alphabet Σ = {0, 1, 2, 3, 4, 5, 6, 7, 8, 9}which recognizes the language {w ∈ Σ^(∗)| w = 3k, k ∈ N}.arrow_forwardRecall the RSA encryption/decryption system. The following questions are based on RSA. Suppose n (=15) is the product of the two prime numbers 3 and 5.1. Find an encryption key e for for the pair (e, n)2. Find a decryption key d for for the pair (d, n)3. Given the plaintext message x = 3, find the ciphertext y = x^(e) (where x^e is the message x encoded with encryption key e)4. Given the ciphertext message y (which you found in previous part), Show that the original message x = 3 can be recovered using (d, n)arrow_forwardFind the sum of products expansion of the function F(x, y, z) = ¯x · y + x · z in two ways: (i) using a table; and (ii) using Boolean identities.arrow_forward
- Give both a machine-level description (i.e., step-by-step description in words) and a state-diagram for a Turing machine that accepts all words over the alphabet {a, b} where the number of a’s is greater than or equal to the number of b’s.arrow_forwardCompute (7^ (25)) mod 11 via the algorithm for modular exponentiation.arrow_forwardProve that the sum of the degrees in the interior angles of any convex polygon with n ≥ 3 sides is (n − 2) · 180. For the base case, you must prove that a triangle has angles summing to 180 degrees. You are permitted to use thefact when two parallel lines are cut by a transversal that corresponding angles are equal.arrow_forward
- Answer the following questions about rational and irrational numbers.1. Prove or disprove: If a and b are rational numbers then a^b is rational.2. Prove or disprove: If a and b are irrational numbers then a^b is irrational.arrow_forwardProve the following using structural induction: For any rooted binary tree T the number of vertices |T| in T satisfies the inequality |T| ≤ (2^ (height(T)+1)) − 1.arrow_forward(a) Prove that if p is a prime number and p|k^2 for some integer k then p|k.(b) Using Part (a), prove or disprove: √3 ∈ Q.arrow_forward
- Provide a context-free grammar for the language {a^ (i) b^ (j) c^ (k) | i, j, k ∈ N, i = j or i = k}. Briefly explain (no formal proof needed) why your context-free grammar is correct and show that it produces the word aaabbccc.arrow_forwardDo College Students With Part-Time Jobs Sleep Less? College students were surveyed about the number of hours they sleep each night.Group A = With part-time jobs | Group B = Without jobs Group A: 6, 5, 7, 6, 5Group B: 8, 7, 9, 8, 7 Instructions: State your hypothesis and perform a two-sample t-test with all formulas. Create histograms for each group. Label axes and add titles. Comment on the distribution shape (e.g., normal, skewed, etc.).Solve on pen and paperarrow_forwardThis is advanced mathematics question that need detailed solutionsarrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
- Algebra & Trigonometry with Analytic GeometryAlgebraISBN:9781133382119Author:SwokowskiPublisher:Cengage
 Mathematics For Machine TechnologyAdvanced MathISBN:9781337798310Author:Peterson, John.Publisher:Cengage Learning,
Mathematics For Machine TechnologyAdvanced MathISBN:9781337798310Author:Peterson, John.Publisher:Cengage Learning,

Algebra & Trigonometry with Analytic Geometry
Algebra
ISBN:9781133382119
Author:Swokowski
Publisher:Cengage

Mathematics For Machine Technology
Advanced Math
ISBN:9781337798310
Author:Peterson, John.
Publisher:Cengage Learning,
Graph Theory: Euler Paths and Euler Circuits; Author: Mathispower4u;https://www.youtube.com/watch?v=5M-m62qTR-s;License: Standard YouTube License, CC-BY
WALK,TRIAL,CIRCUIT,PATH,CYCLE IN GRAPH THEORY; Author: DIVVELA SRINIVASA RAO;https://www.youtube.com/watch?v=iYVltZtnAik;License: Standard YouTube License, CC-BY