
1)
To determine: Whether anyone can read the message.
Introduction:
1)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
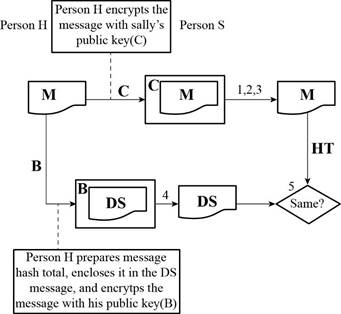
Given diagram:
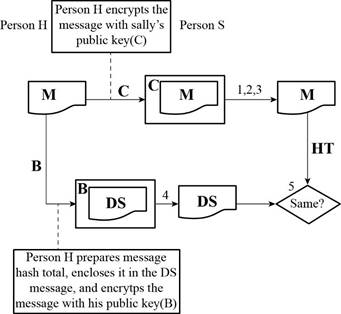
Here,
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether anyone can read the message:
Not everyone can read the message. Only the person who has the private key of Person S can be able to open the message.
2)
To determine: Whether Person S can be sure that the message is from Person H.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
2)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
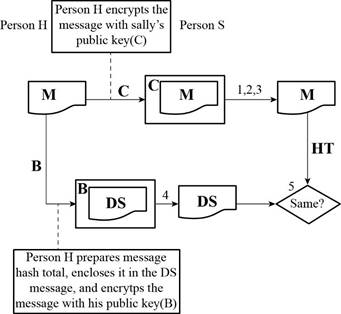
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether Person S can be sure that the message is from Person H:
Anyone with the public key of Person S can be able to send the message
3)
To determine: Whether digital signature message is secret.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
3)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
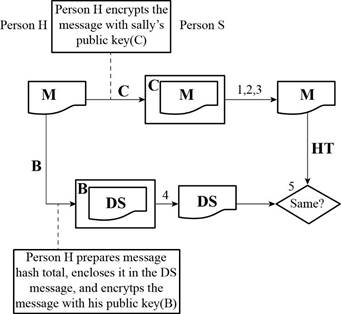
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether a digital signature message is secret:
Anyone with the public key of Person H can be able to open the digital signature message.
4)
To determine: Whether someone other than Person H can send the digital signature message.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
4)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
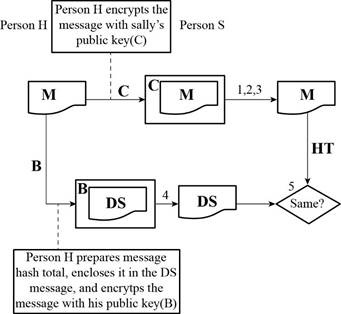
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether someone other than Person H can send the digital signature message:
A person with the private key of Person H can be able to send the digital signature message.
5)
To determine: How Person S know that the message has not been corrupted in transit.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
5)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine how Person S know that the message has not been corrupted in transit:
If the hash total of digital signature equals the hash total that Person S calculated from the message then the message has not been corrupted in transit.
6)
To determine: The sub-part that is related to authenticity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
6)
Explanation of Solution
Determine the subpart that is related to authenticity:
Subpart (2) and Subpart (4) are about authenticity.
7)
To determine: The sub-part that is related to integrity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
7)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to integrity:
Subpart (5) is about integrity.
8)
To determine: The sub-part that is related to confidentiality.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
8)
Explanation of Solution
Given diagram:
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to confidentiality:
Subpart (1) and Subpart (3) are about the confidentially.
Want to see more full solutions like this?
Chapter 9 Solutions
ACCT INFO SYSTEMS (ACCESS CODE)
- Suppose XYZ is a non-dividend-paying stock. Suppose S = $100, σ = 40%, δ = 0, and r = 0.06. What is the price of a 105-strike call option with 1 year to expiration? What is the 1-year forward price for the stock? What is the price of a 1-year 105-strike option, where the underlying asset is a futures contract maturing at the same time as the option?arrow_forwardCalifornia Construction Inc. is considering a 15 percent stock dividend. The capital accounts are: Common stock (6,000,000 shares at $10 par) ....... $60,000,000 Capital in excess of par* ...................................... 35,000,000 Retained earnings ................................................ 75,000,000 Net worth ......................................................... $170,000,000 *The increase in capital in excess of par as a result of a stock dividend is equal to the shares created times (Market price – Par value). The company’s stock is selling for $32 per share. The company had total earnings of $19,200,000 with 6,000,000 shares outstanding and earnings per share were $3.20. The firm has a P/E ratio of 10. a. Show the new capital accounts if a 15 percent stock dividend is given. b. What adjustments would be made to EPS and the stock price? (Assume the P/E ratio remains constant.) c. How many shares would an investor have if they originally had 80 shares? d. What…arrow_forwardRefer to Table 10–6. Price quotes are stated in 1/64ths. What was the closing price of a May 3,990 call option on the S&P 500 Stock Index futures contract on January 13, 2023? Round your closing price answer to 1 decimal place and dollar price answer to the nearest whole number. TABLE 10-6 Option Quotes, January 13, 2023 Underlying Asset: S&P 500 Index (SPX) Closing Value: 3,999.09 Expiration Strike Price Calls Puts Last Volume Open Interest Last Volume Open Interest 04-21-23 3990 140 0 258 164.6 0 223 04-21-23 4010 164.3 257 18,244 144.3 100 17,166 05-19-23 3990 200.7 210 30 169.1 210 52 05-19-23 4010 186.1 303 3,552 279.2 2 3,965 06-16-23 3990 223.3 1 16 178.8 1 1 06-16-23 4010 152.9 0 46 183 1,665 42,159 12-15-23 3975 361 100 2,555 250.1 32 2,438 12-15-23 4025 349.3 0 2,416 268.2 4 2,149 OPTIONS ON INTEREST RATE FUTURES Underlying Asset: March 2023 30-Year Treasury Bond Future Prior Settle: 130'02 Expiration Strike Price Calls Puts…arrow_forward
- Terrill Machining Inc. sells machine parts to auto mechanics. It has not paid a dividend in many years but is currently contemplating some kind of dividend. The capital accounts for the firm are as follows: Common stock (2,400,000 shares at $5 par) . Capital in excess of par* ............................... Retained earnings ......................................... Net worth ................................................... $12,000,000 5,000,000 23,000,000 $40,000,000 *The increase in capital in excess of par as a result of a stock dividend is equal to the new shares created times (Market price – Par value). The company’s stock is selling for $20 per share. The company had total earnings of $4,800,000 during the year. With 2,400,000 shares outstanding, earnings per share were $2.00. The firm has a P/E ratio of 10. a. What adjustments would have to be made to the capital accounts for a 10 percent stock dividend? Show the new capital accounts. b. What adjustments would be made to…arrow_forwardPat’s Video Games has been struggling recently as it has been rumored that the owners are secret Dodgers fans. As a result, its stock price is now only $4 per share. It is going to declare a one-for-two reverse stock split to increase the stock value. a. If an investor owns 90 shares, how many shares will he own after the reverse stock split? b. What is the anticipated price of the stock after the reverse stock split? c. Because it became public knowledge that the owners of Pat’s Video Games were Dodgers fans (and used company proceeds to purchase Dodger paraphernalia, the stock price continued to drop even after the stock split. If the stock price only goes up to 75 percent of the value computed in part b. What will the stock’s price be? d. How has the total value of an investor’s holdings changed from before the reverse stock split to after the reverse stock split (based on the stock value computed in part c)? e. What important lesson did the investor learn?arrow_forwardPurrogi Cat Treats Inc. earned $500 million last year and retained $290 million in earnings. What is the payout ratio?arrow_forward
- Ethical dilemma: Republic Communications Corporation (RCC) has offered you an attractive position in its financial planning division. The new position would constitute a promotion with a $30,000 increase in salary compared to the job you now have at National Telecommunications, Inc. (NTI). The problem is that RCC wants you to bring the rate-setting software you developed at NTI, along with some rate data, with you to the new job. Even though NTI sells its software to other companies and information concerning telephone rates is available to the public, you know that such knowledge will help RCC significantly in its attempt to redesign its rate-setting system. In fact, according to the situation presented in the text, a new and improved rate-setting program could be worth as much as $200 million per year for RCC. Therefore, the question is whether the information RCC wants you to take with you to your new job is proprietary to NTI. Should the rate-setting program and the rate data be…arrow_forwardYour traditional IRA account has stock of GFH, which cost $2,000 20 years ago when you were 50 years old. You have been very fortunate, and the stock is now worth $23,000. You are in the 32 percent income tax bracket and pay 15 percent on long-term capital gains. a. What was the annual rate of growth in the value of the stock? b. What are the taxes owed if you withdraw the funds? Answer to part b. is $8,050 *Please display all work & needed formulasarrow_forwardCan anyone figure this out correctly? I keep getting the wrong answers over and over? Cost of Trade Credit Grunewald Industries sells on terms of 3/10, net 40. Gross sales last year were $4,161,000 and accounts receivable averaged $370,500. Half of Grunewald's customers paid on the 10th day and took discounts. What are the nominal and effective costs of trade credit to Grunewald's nondiscount customers? (Hint: Calculate daily sales based on a 365-day year, calculate the average receivables for discount customers, and then find the DSO for the nondiscount customers.) Do not round intermediate calculations. Round your answers to two decimal places. 1.) Effective cost of trade credit:arrow_forward
- Explain how an increase in interest rates by a central bank could affect bond prices and stock market performance. Explanation.arrow_forwardWhat is the purpose of diversification in an investment portfolio, and how does it reduce risk?arrow_forwardExplain how an increase in interest rates by a central bank could affect bond prices and stock market performance.arrow_forward
- Principles of Accounting Volume 1AccountingISBN:9781947172685Author:OpenStaxPublisher:OpenStax College
 Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,
Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning, Auditing: A Risk Based-Approach (MindTap Course L...AccountingISBN:9781337619455Author:Karla M Johnstone, Audrey A. Gramling, Larry E. RittenbergPublisher:Cengage Learning
Auditing: A Risk Based-Approach (MindTap Course L...AccountingISBN:9781337619455Author:Karla M Johnstone, Audrey A. Gramling, Larry E. RittenbergPublisher:Cengage Learning  Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning
Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning



