
EBK COMPUTER SYSTEMS
3rd Edition
ISBN: 8220101459107
Author: O'HALLARON
Publisher: YUZU
expand_more
expand_more
format_list_bulleted
Concept explainers
Textbook Question
Chapter 8, Problem 8.24HW
Modify the
- 1. Each child terminates abnormally after attempting to write to a location in the read-only text segment.
- 2. The parent prints output that is identical (except for the PIDs) to the following:
child 12255 terminated by signal·11: Segmentation fault
child 12254 terminated by signal·11: Segmentation fault
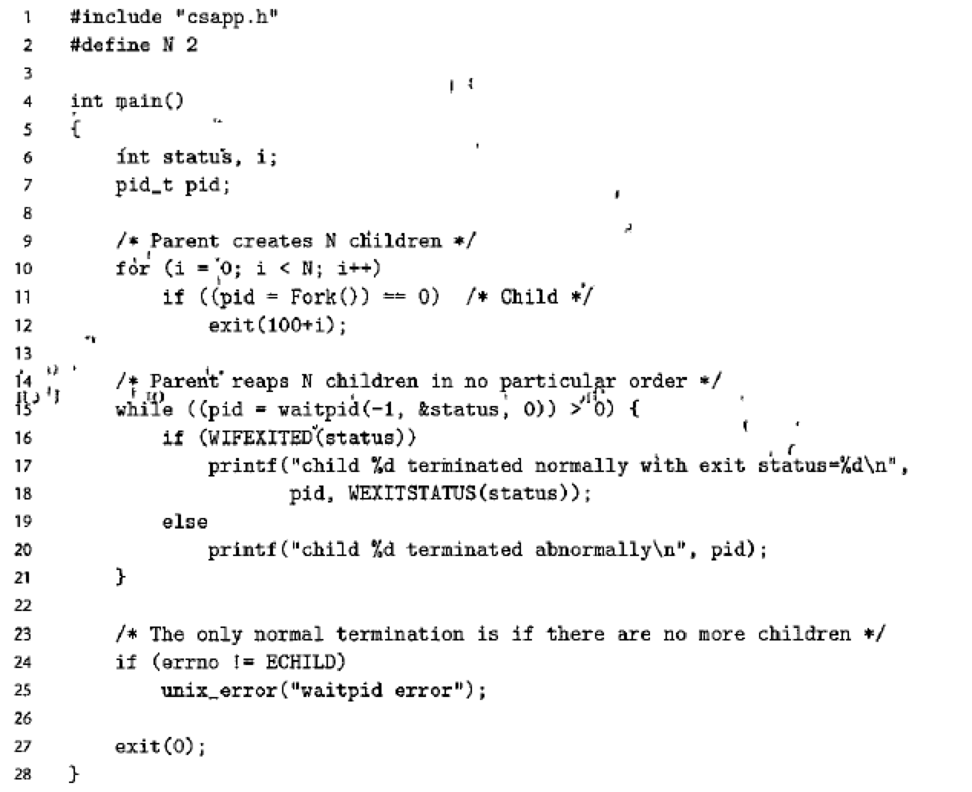
Figure 8.18 Using the waitpid function to reap zombie children in no particular order.
Expert Solution & Answer
Want to see the full answer?
Check out a sample textbook solution
Students have asked these similar questions
(connection)?
Q1: Define the BGP ? Ebgp vs I bgp, and how do I advertise? With a drawing example
QT: Explain how to make messages in the BGP protocol.
Q: What is concept the hot potato routing in BGP?
Q: What are the criteria for BGP route selection?
Qo: Define the concept of Spanning Tree Protocol. Explain in detail and draw the figures.
Q1: What happens when STP is disabled?
QV: Define the concept of broadcast storm.
QA: List and explain the Steps to a Loop-Free Topology when using the Spanning Tree
Algorithm and Spanning Tree Protocol in a four-step process.
I want a typical and concise
Solution
WATCH THE VIDEO ABOUT MODELLING OR SPECIFICATION PHASE AND ANSWER THE FOLLOWING QUESTIONS:
https://www.youtube.com/watch?v=uoIxDeAyfdo
1.- DEFINE SPECIFICATION OR MODELLING
2.- WRITE DOWN THE 3 REQUIREMENTS SPECIFICATION TECHNIQUES OR FORMATS
3.-DEFINE USE CASES
4.-DEFINE SRS
5.-DEFINE USER STORIES
6.- IS IT RECOMMENDABLE TO USE SRS DOCUMENTS IN AGILE METHODOLOGY? WHY?
7.- HOW DO YOU KNOW WHICH TECHNIQUE OR FORMAT TO USE?
8.- WRITE DOWN THE USE CASE COMPONENTS
READING AND LISTENING ACTIVITIES BASED ON THE VIDEO: “REQUIREMENT ELICITATION “
Watch the following video and look for the answer to the following questions:
https://www.youtube.com/watch?v=pSQRetBoaRE&t=24s
1.-NAME THE 2 PHASES OF THE REQUIREMENT ENGINEERING PROCESS
2.-NAME AT LEAST 7 ELICITATION TECHNIQUES TO COLLECT THE INFORMATION REQUIRED
3.-REFER TO THE NUMBER OF QUESTIONS AND TYPE OF QUESTIONS THAT SHOULD BE ASKED TO THE DIFFERENT STAKEHOLDERS.
4.-NAME THE DIFFERENT TYPES OF PROBLEMS YOU CAN ENCOUNTER DURING THE REQUIREMENT ELICITATION PROCESS
5.- ACCORDING TO THE VIDEO, WHICH TYPES OF TECHNIQUES SHOULD YOU USE, WHICH ONES WOULD YOU USE ACCORDING TO PROFESSOR SHERRIFF ‘S RECOMMENDATIONS?
Chapter 8 Solutions
EBK COMPUTER SYSTEMS
Ch. 8.2 - Prob. 8.1PPCh. 8.4 - Prob. 8.2PPCh. 8.4 - Prob. 8.3PPCh. 8.4 - Prob. 8.4PPCh. 8.4 - Practice Problem 8.5 (solution page 797) Write a...Ch. 8.4 - Practice Problem 8.6 (solution page 797) Write a...Ch. 8.5 - Practice Problem 8.7 (solution page 798) Write a...Ch. 8.5 - Prob. 8.8PPCh. 8 - Prob. 8.9HWCh. 8 - In this chapter, we have introduced some functions...
Ch. 8 - How many hello output lines does this program...Ch. 8 - How many "hello' output lines does this program...Ch. 8 - Prob. 8.13HWCh. 8 - How many hello output lines does this program...Ch. 8 - How many "hello lines does this program print?Ch. 8 - Prob. 8.16HWCh. 8 - Prob. 8.17HWCh. 8 - Consider the following program: Determine which of...Ch. 8 - How many lines of output does the following...Ch. 8 - Use execve to write a program called my1s whose...Ch. 8 - What are the possible output sequences from the...Ch. 8 - Write your own version of the Unix system function...Ch. 8 - One of your colleagues is thinking of using...Ch. 8 - Modify the program in Figure 8.18 so that the...Ch. 8 - Write a version of the fgets function, called...
Additional Engineering Textbook Solutions
Find more solutions based on key concepts
In the following exercises, write a program to carry out the task. The program should use variables for each of...
Introduction To Programming Using Visual Basic (11th Edition)
Describe the three types of anomalies that can arise in a table and the negative consequences of each.
Modern Database Management
This optional Google account security feature sends you a message with a code that you must enter, in addition ...
SURVEY OF OPERATING SYSTEMS
Design a Whi1e loop that lets the user enter a number. The number should be multiplied by 10, and the result st...
Starting Out with Programming Logic and Design (5th Edition) (What's New in Computer Science)
1.2 Explain the difference between geodetic and plane
surveys,
Elementary Surveying: An Introduction To Geomatics (15th Edition)
Area Class Write a class that has three overloaded static methods for calculating the areas of the following ge...
Starting Out with Java: From Control Structures through Data Structures (4th Edition) (What's New in Computer Science)
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-engineering and related others by exploring similar questions and additional content below.Similar questions
- Can you please show me how I can do this on google sheets. For the spreadsheet you need to create a multi page sheets thing that uses all the techniques of counts/sums and graph showing how many contracts have been returned for each grade...you can make up the data (let's say in grade 9 I got 15 contracted back with fake data that I want you to show me how to create on google spreadsheet) For grade 10 i got 20 contracts signed, for grade 11 I got 16 contracts and for grade 12 I got 25 contracts back. Can you help me pls. Thanks so much. Make sure you have graphs on the page and also the sum written as a formula and the numbers filled in the columns.arrow_forwardI need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forwardGoal: Understand how to build a concurrent server and deal with signals Description: Use TCP socket programming in C to implement a pair of client and server programs. The client simply asks the user to enter a string (null-terminated), and then displays a menu for the user to select an operation on that string. The string and the type of operation are sent to the child server which performs the required operation and returns the result back to the client. That is, the server (parent) creates a child for each request of the client (you need to print the port and IP address of the client on the server terminal). Then it waits for the child to finish processing client's request and prints the process ID of the terminated child. The connection between your client and server should stay open, so that the client can send another request. However, the exit will happen when the user sends the client program the SIGQUIT signal. The handler will print a notifying message (for example, "Good…arrow_forward
- I need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forwardI need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forwardI need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forward
- I need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forwardI need help with this problem and an step by step explanation of the solution from the image described below. (Introduction to Signals and Systems)arrow_forwardQ1.A. Sketch a graph of f(x), then find the Fourier series of f(x) for three values and has a period of 2π. (8 marks) f(x) = { x² x²sin 3x -π≤ x ≤ 0) 0 ≤ x ≤ narrow_forward
- Q3.A. Given the flow graph below, Find the H(z)? x(z) y(z) (7 marks) z-1 ↓arrow_forwardQ2.A. Find the inverse Z-Transforms using partial fraction method of the following function: (8 marks) Z-1 F(z) = 2+3Z-1 + (1-2-1) (1-12-12arrow_forwardI've been having trouble solving this problem from my engineering analysis class textbook.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY
Computational Software for Intelligent System Design; Author: Cadence Design Systems;https://www.youtube.com/watch?v=dLXZ6bM--j0;License: Standard Youtube License