Below is an example of key generation, encryption, and decryption using RSA. Look at the example, then fill in the blanks to indicate what each part is or answer the question. You do not have to do any math for this. Here are the words to select from to fill in the blanks. Modulus, encrypt key, decrypt key, factor, plaintext, ciphertext Public key is (23, 11) What is 23 called?_ Private key is (23, 13) What is 23 called? 23 can be part of the public key because it is very hard to ENCRYPT (m) = m^e mod n What is m? DECRYPT (c) = c^d mod n What is c? What is 11 called?_ What is 13 called?_ what is n? large prime numbers. (generic name, not a number)
Below is an example of key generation, encryption, and decryption using RSA. Look at the example, then fill in the blanks to indicate what each part is or answer the question. You do not have to do any math for this. Here are the words to select from to fill in the blanks. Modulus, encrypt key, decrypt key, factor, plaintext, ciphertext Public key is (23, 11) What is 23 called?_ Private key is (23, 13) What is 23 called? 23 can be part of the public key because it is very hard to ENCRYPT (m) = m^e mod n What is m? DECRYPT (c) = c^d mod n What is c? What is 11 called?_ What is 13 called?_ what is n? large prime numbers. (generic name, not a number)
Database System Concepts
7th Edition
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Chapter1: Introduction
Section: Chapter Questions
Problem 1PE
Related questions
Question

Transcribed Image Text:Below is an example of key generation, encryption, and decryption using RSA. Look at the example, then fill in the blanks to indicate what each part is or answer the question. You do not have to do any math for this. Here are the words to select from to fill in the blanks.
Modulus, encrypt key, decrypt key, factor, plaintext, ciphertext
Public key is (23, 11) What is 23 called? ____________, What is 11 called?____________
Private key is (23, 13) What is 23 called?____________, What is 13 called?____________
23 can be part of the public key because it is very hard to ____________ large prime numbers.
ENCRYPT (m) = m^e mod n What is m? ____________, what is n? ____________ (generic name, not a number)
DECRYPT (c) = c^d mod n What is c? ____________
Search for the following.
What does "mod" mean?

Transcribed Image Text:**Example: Generating an RSA Public-Key/Private-Key Pair**
An RSA public-key/private-key pair can be generated by the following steps:
**1. Generate a pair of large, random primes p and q. Note:** For examples, we use small prime numbers due to the size of the number generated.
- **p = 3, q = 5**
**2. Compute the modulus n as n = pq.**
- **n = p * q, 15 = 3 * 5**
**3. Select an odd public exponent e between 3 and n-1 that is relatively prime to p-1 and q-1.**
- \( e \) is between 3 and 14, \( e \) is relatively prime to 2 (3-1) and 4 (5-1)
- \( \phi(n) = 2 * 4 = 8 \)
- **e = 7, could also be 9 or 11 or 13**
**4. Compute the private exponent d from e, p, and q.**
- **\( e \times d \equiv 1 \pmod{\phi(n)} \)**
- **\( 7 \times d \equiv 1 \pmod{8} \)**
**5. Calculate d:**
- **\( 7 \times d \equiv 1 \pmod{8} \)**
- What number multiplied by 7 and then divided by 8 equals 1?
| Multiples of 8 | **8** | 16 | 24 | 32 | 48 | 56 | 64 | 72 | 80 | 88 | 96 | 104 |
| --- | --- | --- | --- | --- | --- | --- | --- | --- | --- | --- | --- | --- |
| Multiples of 7 | **7** | 14 | 21 | 28 | 35 | 42 | **49** | 56 | 63 | 70 | 77 | 84 | 91 |98 | 105 |
- **\( 7 \times 15 \equiv 1 \pmod{8} \) = 105/8 = 13 remainder 1**
- **d = 15**
**6. Output (n, e) as the public key and (
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 3 steps with 2 images

Follow-up Questions
Read through expert solutions to related follow-up questions below.
Follow-up Question
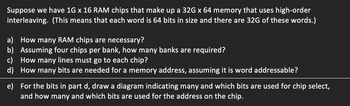
Transcribed Image Text:Suppose we have 1G x 16 RAM chips that make up a 32G x 64 memory that uses high-order
interleaving. (This means that each word is 64 bits in size and there are 32G of these words.)
a) How many RAM chips are necessary?
b) Assuming four chips per bank, how many banks are required?
c) How many lines must go to each chip?
d)
How many bits are needed for a memory address, assuming it is word addressable?
e)
For the bits in part d, draw a diagram indicating many and which bits are used for chip select,
and how many and which bits are used for the address on the chip.
Solution
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:
9780133976892
Author:
Paul J. Deitel, Harvey Deitel
Publisher:
PEARSON

Database Systems: Design, Implementation, & Manag…
Computer Science
ISBN:
9781337627900
Author:
Carlos Coronel, Steven Morris
Publisher:
Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:
9780073373843
Author:
Frank D. Petruzella
Publisher:
McGraw-Hill Education